Identity and access management, sometimes simply known as identity management, refers to the IT function of maintaining security through the management of digital identities. In a workplace, this includes provisioning employees with accounts to all applications and platforms they will be using for their official tasks, assigning them with the right kind of permissions to each of these applications/platforms, and making sure that the right people have the right access to the right resources and data.
Identity and access management also involve defining and determining:
- The identity of each employee/user and the roles that they are assigned
- The correct levels of protection for sensitive data and applications
- The steps involved in authorizing and authenticating users before they are provided access
- The importance of identity and access management
Now, more than ever, organizations are dependent on numerous applications for their operations. According to a study, an organization uses 16 SaaS apps on average. In addition to this, there will be custom-built on-premise and cloud applications adding to this list.
As functionally useful as they are, each of these applications is also a gateway to the organization’s data. Hackers often target these applications to break into the enterprise network. That’s why a weak credential, an idle account, or access that hasn’t been revoked after an employee has left the organization may all be threats to the organization itself. That is also the reason why identity and access management becomes so important!
What’s more, the risk of data breaches is now greater than ever with brute force attacks, social engineering and other smart technology assisting hackers to steal others’ identities online. Identity and access management, therefore, becomes all the more important – a stolen identity can be promptly revoked access with an efficient system in place.
Identity and Access Management Essentials
Secure the sign-in process
Set up a strong password policy, enable multi-factor authentication to prevent access by unauthorized persons in the case of a credential compromise.
Secure your devices
Create and enforce policies and restrictions for use of company-owned and personal devices and set up restrictions so that business-critical data is only accessed from “safe”, “recognized” devices.
Stay up-to-date
Update all tools, platforms, and applications regularly as patches and upgrades are introduced often to reinforce security from the latest cyber attacks.
Provision and deprovision promptly
As user roles change and evolve within the organization, make sure that you promptly change access level permissions, revoking access to unwanted/irrelevant applications. When an employee leaves, be equally prompt in removing all access.
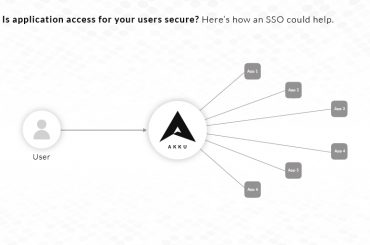
Opt for SSO
A single sign-on solution brings all of the organization’s applications to a centralized platform. With an SSO in place, you no longer need to login to each application separately to provide/change/revoke permissions to users; you can do them all from a single dashboard.
Set up a geo-fence
With cloud-based applications making it possible for users to access applications from literally anywhere in the world, attacks can also come from anywhere in the world! Whitelist only the countries/regions you know that your employees are likely to access their applications from, and block off access from other regions to cut down your risks.
Counter smart technology with smarter technology
Manually managing identity and access is a tedious process, especially in the current context where smart technology aids cybercriminals. One of the most efficient ways to manage identity and access in such a setting would be through the use of an identity and access management (IAM) solution like Akku.
Akku is designed to help you customize strong policies to protect your business data, prevent access in case of suspicious login attempts, and stay in control of all activity across the length and breadth of your organization’s network of on-premise and cloud-based applications.
It doesn’t stop there! In addition to protecting your data and applications, Akku is also designed to boost employee productivity and maintain compliance with standards. Want to know more? Get in touch with us for a free demo!