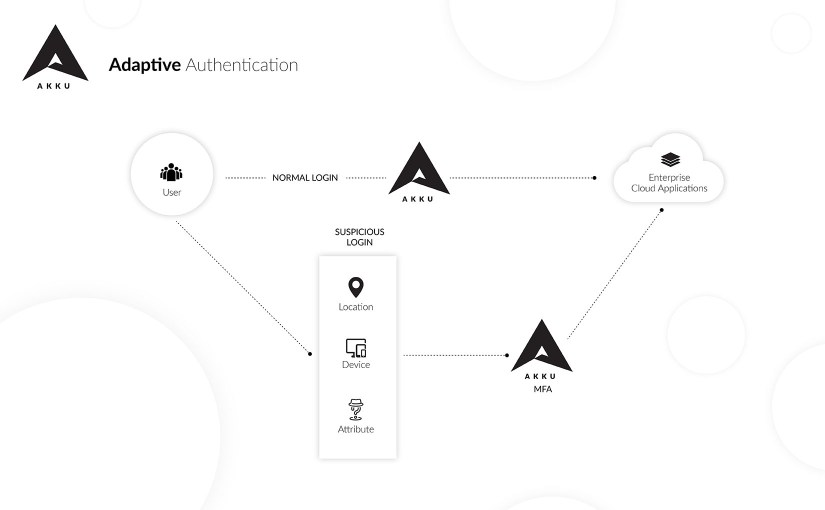
Adaptive authentication, method for enforcing the right authentication factors depending on users profile and tendencies. It acts to balance the level of trust against risk.
Adaptive authentication is the way that two factor authentication or multi factor authentication can be configured or deployed.
A multi-factor authentication function can either be set to run at every single login, or to be triggered only in cases where the authentication risk of a login attempt is identified as being suspicious or high-risk.
The latter case is referred to as Adaptive Authentication, and there are several types of events that can trigger this.
Environment-based Authentication
This occurs when users are authenticated based on environmental factors such as geographic location. The probability of the user being legitimate is checked by using the device location, identifying unlikely travel routines, and blocking users in blacklisted locations.
Device-based Authentication
When the levels of security used for authentication dynamically change based on the properties of the device being used to request for authentication, device-based authentication is performed.
Attribute-based Authentication
Attribute-based authentication occurs when attributes assigned to users are used to authenticate users in different levels. Users can be grouped into separate user stores and different authentication schemes can be implemented for each user store. Other common attributes that are considered for authentication include user age, user type, and user roles.
Behavior-based Authentication
There are 2 ways to perform behavior based authentication – through user behavior and the use of geo-velocity.
Risk-based Authentication
Risk-based authentication is used when users are granted access based on a risk score calculated for a certain series of events. Various factors are considered by the risk calculating algorithm, such as the size of the user base, sensitivity of the resources requested, criticality of the system, geolocation, IP addresses, and the status of firewalls and anti-virus software of the device.
Through the use of adaptive authentication methods, the power of MFA can be harnessed in a highly effective manner, maximizing security while avoiding unnecessarily delayed logins.
Akku, the identity and access management solution by CloudNow delivers a powerful multi-factor authentication function to keep your data and applications secure. Contact us for more information today!