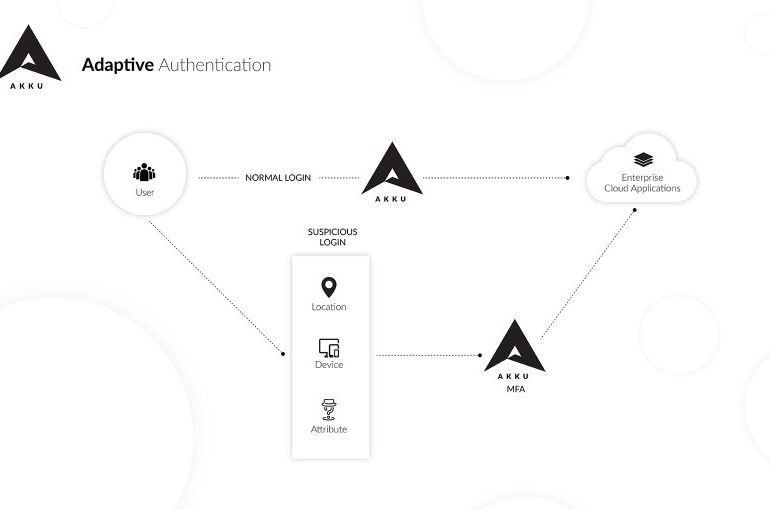
Google Cloud Platform (GCP) IAM comes as a free service that is available by default to all users of the Google Cloud Platform. GCP IAM is Google’s identity management console, enabling administrators of organizations to manage access and permissions provided to employees across the range of applications and resources that come as part of the Google Cloud Platform. The main function of the IAM is to grant specific users/roles with access to specific GCP resources and prevent unwanted access to other resources.
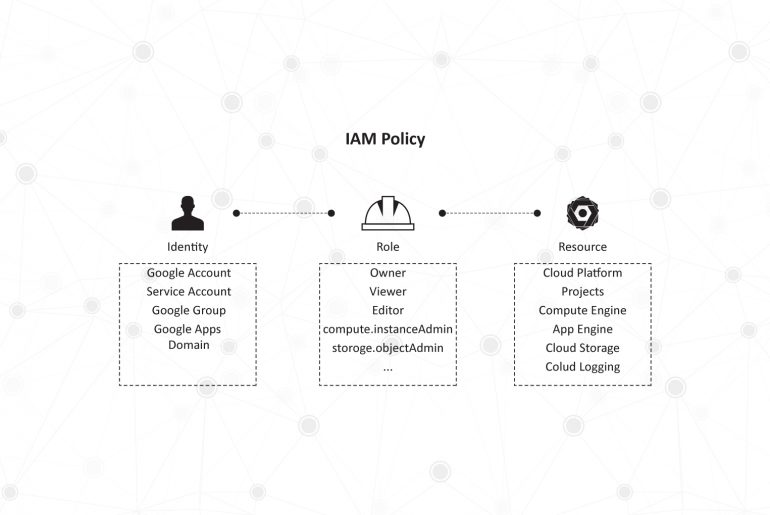
The fundamental building block of GCP IAM is an IAM Policy which answers the question of who (identity) has what access (role) to which data or applications (resource). This IAM Policy is made up of permissions, bundled into roles and matched by identities.
Let’s take a closer look at the concepts of identity, role, and resource as defined by GCP IAM, which make it a useful IAM solution.