The synergy between Identity and Access Management (IAM) and IT, cybersecurity, and admin departments of an organization is obvious, but…
Identity Access Management (IAM) is a collective term that covers processes and policies to manage user identities and regulate user…
Process reliability, transparency, traceability, and flexibility – the four aspects of modern IT security. An Identity and Access Management solution…
In any enterprise, it is a given that employees will come and go, and many will switch roles within the…
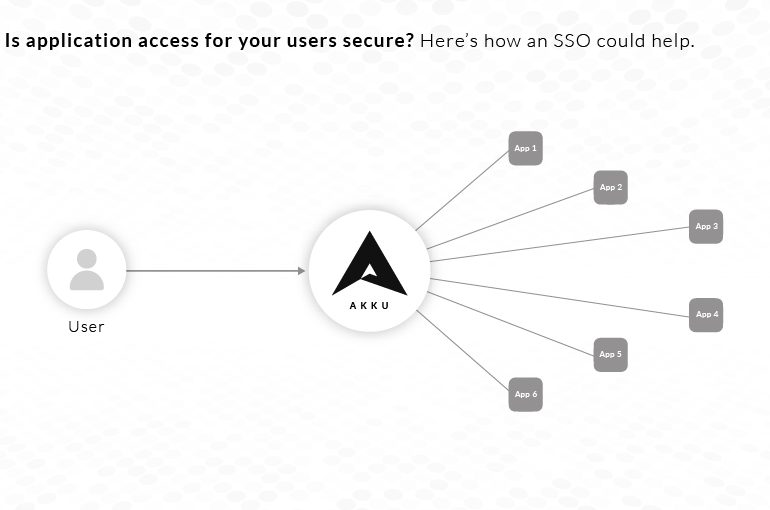
Single Sign-On (SSO) is a session and user authentication service where one set of credentials – typically a username and…
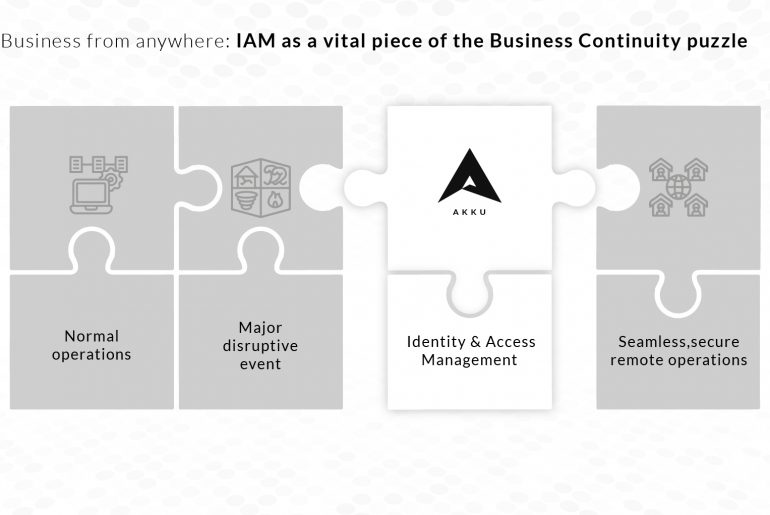
COVID-19 was a shock to the global economy. The pandemic aside, the enforced and voluntary closure of offices has dramatically…
Many enterprises have built their cybersecurity around their firewalls. But increasingly, the firewall is losing favor in modern enterprises with…
Remote working has impacted the world of cybersecurity in multiple ways. Remote workers are often not protected by enterprise-level security…
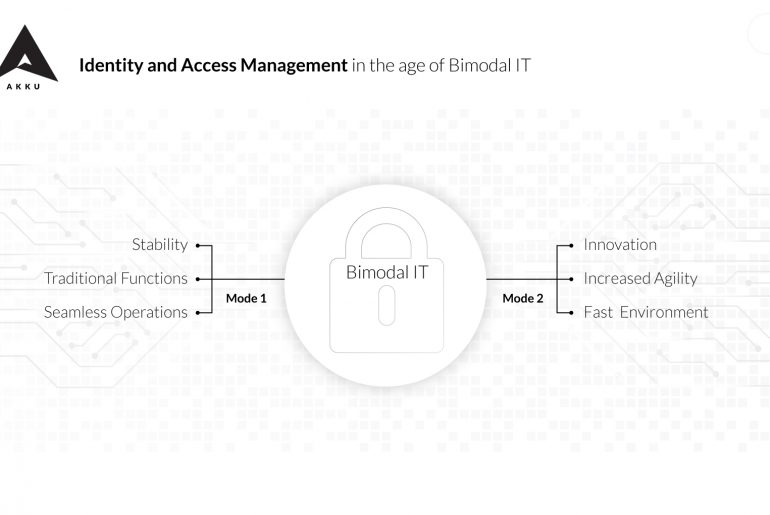
An important new practice that has emerged over the past few years in IT management is Bimodal IT, defined by…
Healthcare organizations are unique in the volume and sensitivity of information that they hold. Reports say that healthcare is among…