Active Directory is quite simply the most popular identity management solution for enterprises in the world. An incredible ~90% of…
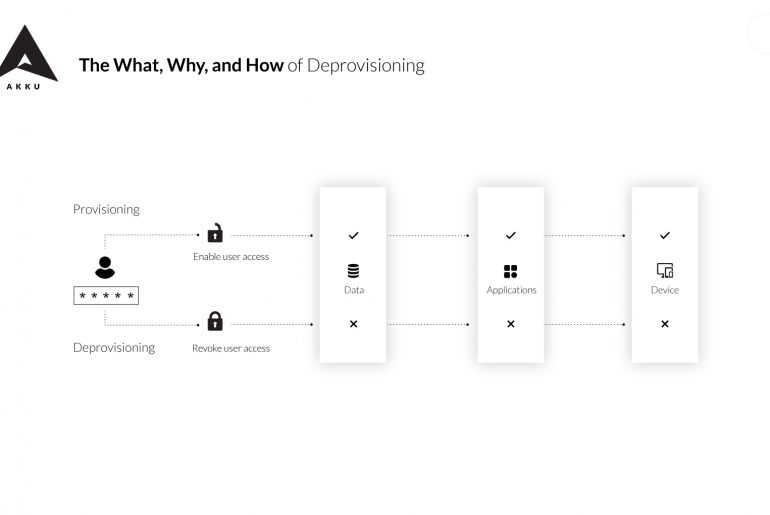
What’s deprovisioning? Simply put, deprovisioning is the opposite of provisioning. While provisioning is carried out when an employee joins the…
With each passing year, newer technologies emerge and companies of all sizes adopt them to keep up the competitive, ever-changing…
The manufacturing industry took a big hit at the start of the pandemic-imposed lockdown, mainly due to two reasons. Firstly,…
[wonderplugin_gallery id=1] “Digital transformation” has been a buzzword well before the COVID-19 pandemic hit. In those pre-COVID times, digital transformation…
[wonderplugin_gallery id=1] Data-driven decision-making (DDDM) is the process of using insights drawn from data to aid the process of decision…
Ever wondered why organizations emphasize the importance of setting a complicated password as opposed to something convenient like ‘password123’? In today’s world, hackers are getting creative with their cybersecurity attacks. One type of attack that has gained a lot of traction in the past year is ‘password spraying’ – a type of brute force attack in the cybersecurity realm that goes beyond the traditional forms of hacking into an account.
Picture this – in the past, hackers would attempt to gain unauthorized access to a single account by constantly guessing the password in a short period of time. But with organizations bringing measures such as locking an account when three or more attempts have been made, the user gets notified about any attempted security breach.
Compliance ensures that an enterprise maintains a minimum standard of security-related requirements in accordance with industry and regulatory standards. Its scope, however, goes beyond having regulations in place, to successfully implementing policies and contracts.
As security breaches, fraud, and theft of data are becoming increasingly widespread in the IT world, industry guidelines for compliance have become more complex, and enterprise policies more elaborate. Adding to the difficulty of achieving security compliance is the limited functionality of network security tools in dealing with the dynamic nature of the cloud.
Today, migrating to the cloud is a crucial stage in a financial enterprise’s growth and development. It is, quite simply, the most efficient way of running operations. With this in mind, financial services organizations are investing significant resources in cloud-based technologies, including infrastructure, platform, and software as a service.
Digital transformation has been adopted by most companies from around the world, resulting in a more connected and innovative business environment. Today, digital transformation essentially involves an organization’s adoption of IoT, cloud computing, machine learning, and AI.