The education industry faces unique identity and access management challenges; different education systems have specific IAM needs that depend on their environment. The central challenges include:
The year 2019 has been a significant one in the technology world, with several high profile cases grabbing headlines. In fact, according to a recent article by DataQuest India, there were at least four areas of interest which were highlighted this year – Remote Desktop Protocol (RDP) threats, showstopper vulnerabilities like in the case of URGENT/11, speculative execution vulnerabilities such as Meltdown and Spectre, and finally the many ransomware attacks.
As we move on to a whole new decade, it’s important to take stock of what the past decade has taught us and what the future has in store. In the cybersecurity world, experts bear past experiences in mind and routinely predict a number of innovative techniques that could be used to infiltrate security systems. Each year, different methods and new approaches are introduced or discussed, touching upon all those concerns about data protection and the challenges ahead.
Approximately two billion records were stolen between July and October 2019. That’s just in one quarter of a year! This is several times more than what was stolen last year – half a billion records. Even as organizations continue to invent new technology and pump in more and more funds (an estimated $124 billion in 2019) to secure data, the number of breaches also continues to rise – at an alarming rate!
It’s becoming evident that cybersecurity software solutions alone are not enough anymore. There is an urgent need to train employees and bring in experts who can close the loopholes left by software solutions. Therein arises the concept of offensive security.
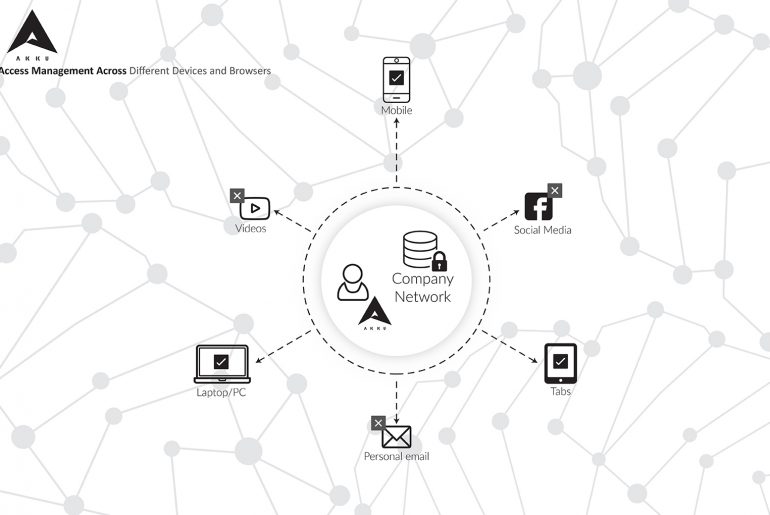
In today’s technology ecosystem, a strong foundation for authorization plays an important role in the overall data security of a company. Controlling each user’s access to data, and monitoring this across devices and browsers is essential to your enterprise’s security.
Implementing a strong device policy is an integral aspect of data security
With a strong device policy in place, it is possible to exercise highly granular control over which of the company’s applications, information, and data your employees can access– through the company’s devices, as well as through their personal devices.
Identity and access management, sometimes simply known as identity management, refers to the IT function of maintaining security through the management of digital identities. In a workplace, this includes provisioning employees with accounts to all applications and platforms they will be using for their official tasks, assigning them with the right kind of permissions to each of these applications/platforms, and making sure that the right people have the right access to the right resources and data.
According to the PwC 21st Annual Global Survey, reliability, congruence, consistency, and transparency are the four pillars for building trust among customers and other stakeholders. The same survey also found that 65% of CEOs are concerned about declining trust in business. If you have the same concern, here are some useful suggestions!
When in action, a social engineering attack could look like an email received from a government organization or your own organization asking your employees to divulge their credentials. The basis of social engineering attacks is to induce fear or urgency in unsuspecting users and employees into handing over sensitive information. Over the years, these attacks have become more sophisticated – even if you open a mail or message from a possible attacker, malware is immediately installed on your system.