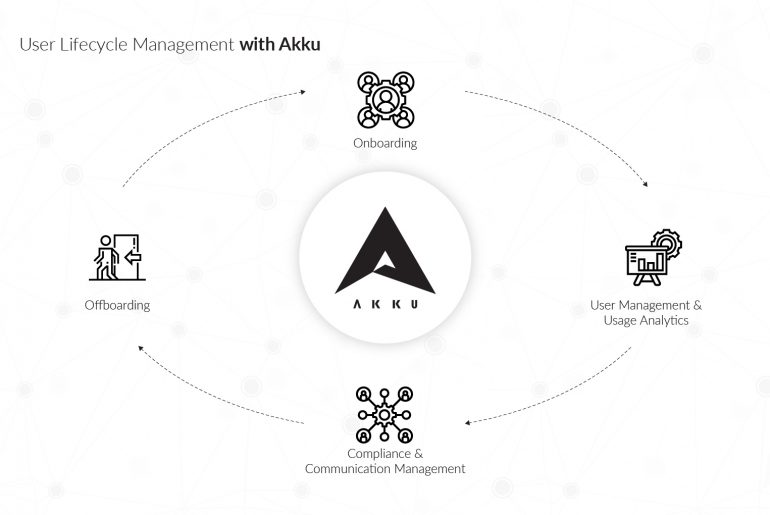
The employee lifecycle is an HR model that identifies the different stages an employee goes through during his/her stint at an organization. Employee lifecycle management, therefore, involves the steps taken by HR in optimizing the flow of the cycle. Typically, the employee lifecycle involves the following stages: recruiting, onboarding, training and development, retention, and offboarding.
In modern organizations, where the employee is also a user (of one or more applications), a similar user lifecycle begins at the onboarding stage and continues until the employee exits the organization.