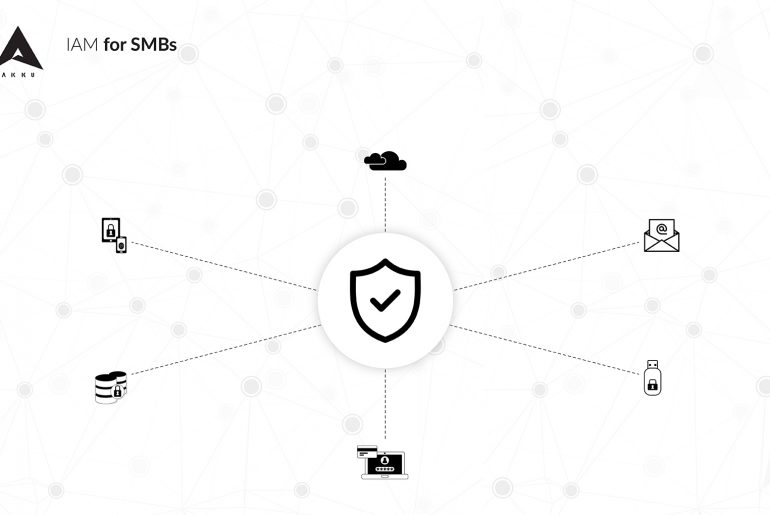
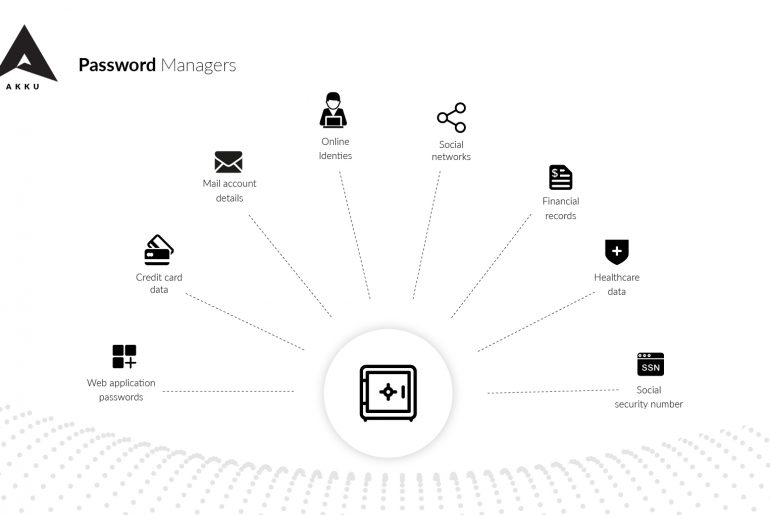
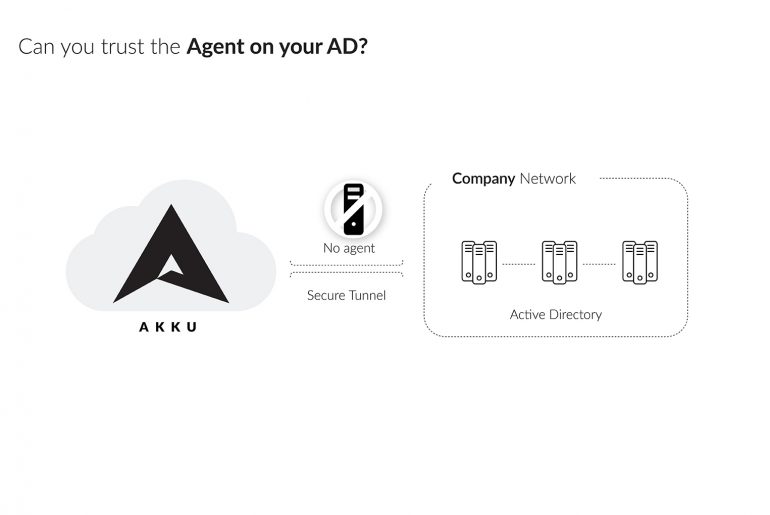
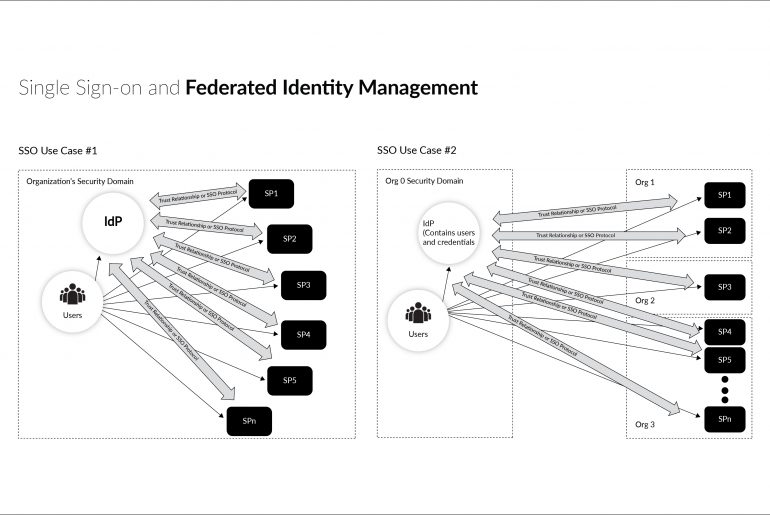
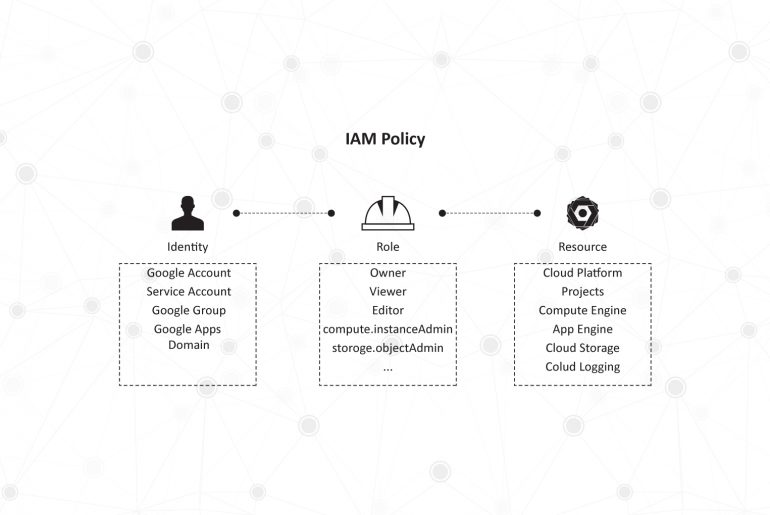
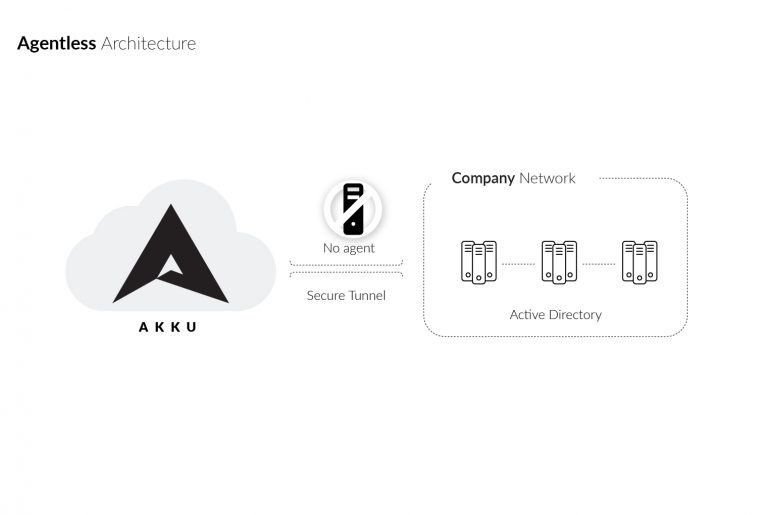
Privilege abuse – that is the security threat that your business’s IT team is most worried about. According to a survey conducted in March 2014 among more than 4000 IT security executives, over 88% of them fear that users who have access to the organization’s applications and data are the ones who are most likely to compromise it and lead to a security breach.
Privilege abuse, or privileged user abuse, refers to the inappropriate or fraudulent use of permitted access to applications and data. This could be done, either maliciously, accidentally or through ignorance of policies. In addition to causing financial losses, such insider breaches also damage the organization’s reputation, sometimes irreparably.