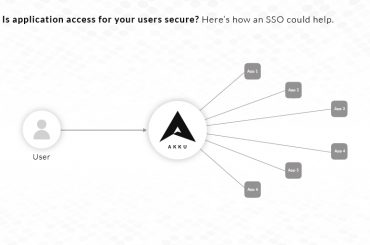
An Identity and Access Management (IAM) solution allows organizations to manage user access to critical data. It is an intermediate layer between your users and your applications/data.
Deploying an IAM solution a proven way to improve network security in an organization. A good IAM solution should also reduce the time spent by your IT team to grant access for individual applications, thereby improving architectural simplicity and reducing the load on your servers. This also means that your users have to remember only one set of credentials to access several applications in your on-premise or cloud network.
What should you expect from a good IAM solution?
Streamlined User Access
An effective IAM solution should greatly reduce hassle by providing a slick and time efficient method to validate users. It should be able to do this without compromising on security, allowing only legitimate users to access your network from on-premise or remote systems.
Conventionally, at organizations that have numerous applications on their network, users need to remember multiple sets of credentials, which is inconvenient, but more secure. An effective IAM solution should be able to strike the right balance between the two extremes of convenience and security.
With a single set of user credentials to access all permitted applications and data, memorizing multiple credentials is avoided, improving productivity and ease of use.
Improved Security
Another important feature you should look out for is the ability to control user access to your network. This is typically delivered through device- and IP-based restrictions, which give you the ability to provide access only from specific devices or IP addresses to your network. In addition to simply whitelisting specific requests, an IAM solution should also be able to permanently block illegal access from blacklisted devices and IPs.
Seamless Admin Control
An identity and access management solution should give the administrators of your network a simple and intuitive dashboard with all the controls needed to secure your network and manage access across it. This can go a long way in reducing the cost and time for your IT team.
This includes managing creating and removing user accounts, as well as controlling the level of access provided to each individual user.
Identity and Access Management by Akku
Akku by CloudNow is a state-of-the-art Identity and Access Management solution for all your user management needs. Its powerful SSO function simplifies user identity and access management, IP- and device-based restrictions prevent unwarranted access, multi-factor authentication reinforces security, and a range of other versatile features put you in complete control of your network. Get in touch with us now to know more!