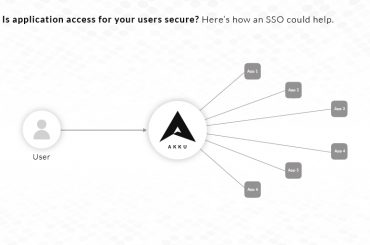
For organizations, it is crucial to ensure data security and, therefore, IAM has become a crucial part of every network security effort. Identity and access management at the organization-level – mostly include IAM solutions for enterprise applications used by organizations to authenticate and validate employees and a relatively small number of users. But how different is the situation with B2C businesses and other organizations who have huge numbers of internal and external users using their online services every day?
For example, for a company like Amazon, which has millions of users using the platform every day, it is important to seamlessly integrate identity and access management with users’ shopping experience. For B2Cs and organizations with a large volume of users, customer experience is as important as application and data security. And customers share critical information such as their bank and card details with the online retail store, which means that ironclad security is required to protect thousands of accounts. At the same time, if application security takes precedence over user experience, it can make for a patchy experience for users who are interacting with your brand. And for brands, an excellent customer experience directly correlates with improved sales, and thereby, improved revenue.
CIAM for improved security
This is where CIAM comes into the picture – customer identity and access management can be a game-changer in striking the right balance between application security and user experience. An efficient CIAM solution should allow your application’s users to register themselves with you and self-manage their accounts every time they log-in. The provisions which allow the usage of these features are similar to regular Identity and Access Management – single sign-on, multi-factor authentication, and data governance capabilities.
One of the biggest advantages of CIAM is that it can be deployed on-premise, in private clouds or even iDaaS platforms. The functionalities and features of CIAM are then built and integrated into applications using REST APIs.
Another similarity between CIAM and the classic IAM is that both fall under the purview of privacy regulations like GDPR. While it may seem like IAM can handle all the use cases of CIAM and that the line differentiating the two is blurry, there are a few features that an efficient CIAM is required to possess.
CIAM should provide organizations with branding control to ensure that users have a seamless transition from the authentication module to the application module. A CIAM is also expected to manage user consent and profile personalization, both of which are not required as critical functionality by organizations which create applications for their employees.
Our exhaustive experience with identity and access management allows us to guide organizations in choosing the best security solutions for their applications. Akku from CloudNow is one such solution which allows organizations to exercise high-level security across their network. To know more, get in touch with us now.