Only a small percentage of people across industries understand the difference between Identity Management and Access Management. The two concepts are certainly related and intricately interwoven, but they are still distinct in meaning and function.
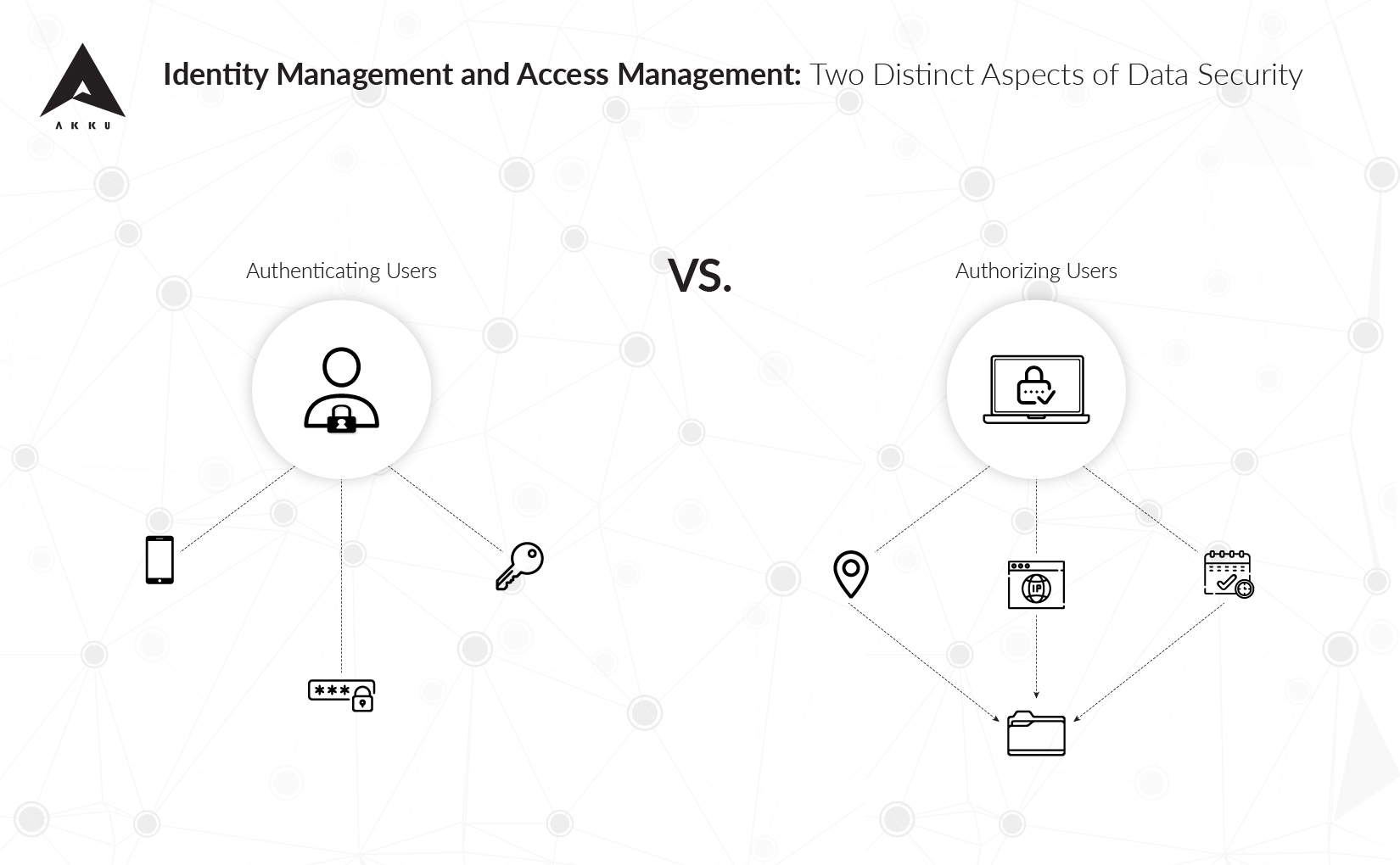
- Identity Management refers to the authentication of users. It deals with managing each user’s attributes
- Access Management refers to the authorization of users. It deals with evaluating user attributes against policies to make yes/no decisions
When authentication and authorization systems are not properly aligned, the overall security system around your enterprise’s data is compromised. This serious issue can sometimes be traced to a lack of understanding of the fundamental distinction between the two concepts of Identity and Access.
What is ‘Identity Management’?
An employee establishes his identity when he officially registers with the company as a user with certified credentials. During the process, his attributes are collected in order to help the organization define his position and role as an employee.
Identity Management refers to the concept of determining who the user is, and managing his attributes. Having a user login and password is the most simple way of determining a user’s identity. With the SSO (single sign-on) function, a user can gain real-time access to a range of data after signing in just once; similarly, his access is terminated with a single sign-off.
The authentication process can be further secured through the use of MFA (multi-factor authentication), which would require users to provide two or more factors of identification. Thus, even if a hacker enters one factor of identification into the system, he would be unable to log in unless he had access to the second one.
A strong authentication system entails protecting all the attributes associated with a single user, ensuring that his identity cannot be duplicated by anyone else.
What is ‘Access Management’?
‘Access’ decisions are, in essence, Yes/No functions that help an organization monitor authorization. Access control is deployed with the power of making a Yes/No decision when it comes to allowing users to access system data and resources.
Access management refers to the concept of determining what information the user can access once his identity is established. When an employee’s credentials are verified, the system should determine what his authorization is.
With device-based and IP-based restrictions in place, permission for authorization is provided for an individual user, through the SSO, to different applications and data. Thus, with a strong access management system in place, you have a better system of monitoring, and you gain tighter control of your employees’ productivity and workflow.
A Single Solution for Data Security that Covers all the Distinctions
As we have seen so far, Identity Management and Access management are closely tied together, but they are distinct in function. To protect the important information that is unique to your enterprise, you require control of a system that aligns the two concepts while being flexible to cover all the functions that are distinct to each.
CloudNow’s Akku is a robust and flexible Identity and Access Management solution which takes care of all aspects of data protection, ensuring there is a clear network of security around the organization.
Get in touch to find out more!