Cloud technology has broken several operational barriers to make remote data access easy. It allows you to scale your business with minimal cost while securely holding business-critical data and applications. But with all these advantages comes a catch – managing personnel access for all the applications and files in your network has become increasingly cumbersome.
Why does your organization need an Identity and Access Management Solution?
Managing the credentials of all your employees across all the verticals of even a small to mid sized organization is time-consuming. It can drain the productivity of your company’s Human Resource and IT management teams. They are valuable resources who could otherwise focus on their core competencies to help you grow your business.
In addition to this, securing your network from breaches and other threats can be challenging with so many people accessing your cloud from various devices and locations. If your network is compromised, all your critical business data is compromised along with it.
This is where an Identity and Access Management (IAM) solution can come in handy. It allows you to seamlessly manage access while protecting your cloud network from breaches.
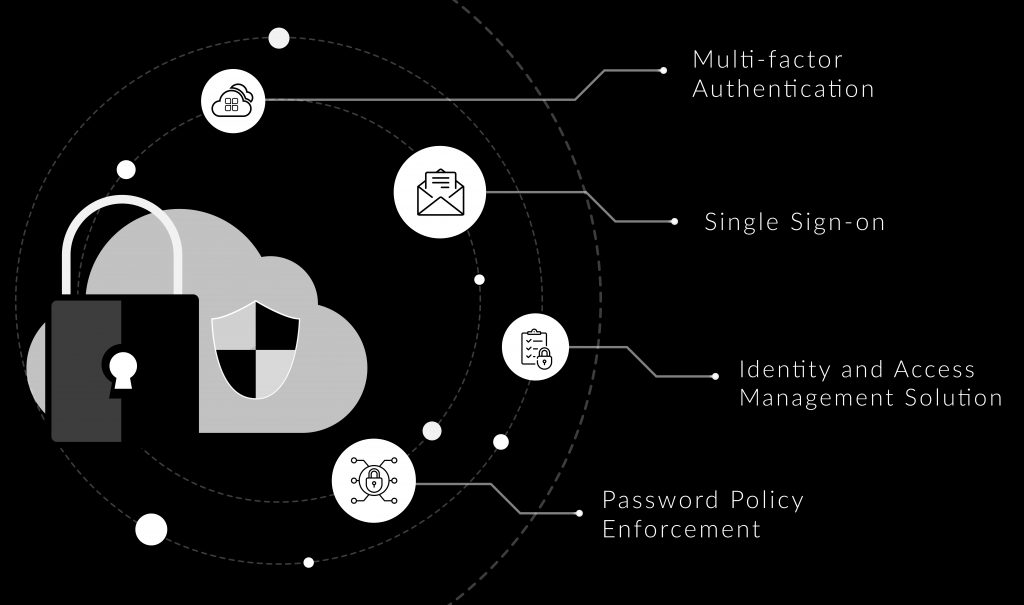
Building blocks of an IAM solution
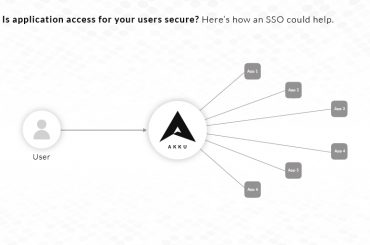
A strong Single Sign-on (SSO) function is at the heart of an IAM solution. The first step in implementing an SSO is to determine and streamline the role of the identity provider (IdP). The IdP is responsible for bringing all the applications and data on your cloud network to a centralized platform. From this platform, access and identity services are managed through a customized Security Assertion Markup Language (SAML). When a high end, customizable SAML is integrated with your enterprise cloud network, it can result in a secure Single Sign-on solution.
With a cloud SSO setup, you can provide each member of your organization with single login credentials for any or all the applications in your cloud network. With your own powerful Identity Provider, you can redirect all access authentications to a safe and fast network. With this setup in place, it is possible to consolidate a single node in your network to control access to your entire organization’s cloud network.
Features of an IAM System
With an efficient Identity and Access Management system, you can accomplish so much more than just rudimentary monitoring of your cloud network. It will come with a well rounded set of features which allows you to control your cloud in a convenient platform. If your network is fitted with a powerful cloud IAM solution, it will automatically come with provisions in place to handle password standardization and multi-factor authentication frameworks.
Single Sign-on
Allocating a single set of credentials for your employees to access relevant data and applications is made easy by implementing an SSO solution for your cloud network. As the admin of your network, it also becomes simple for you to handle access operations in a single dashboard. In addition to this, if the need arises for a user to be removed, it can be done in a few short steps instead of removing access individually for all your applications. When all of this comes together seamlessly, it results in improved productivity across your organization.
Multi-factor Authentication
Sometimes, in spite of the password protection measures you have implemented to secure your cloud, you might feel the need to bring in an additional layer of security to protect all your critical business applications. When that need arises, a well structured IAM solution allows you to keep in place, a multi-factor authentication system. It ensures that your system is insulated against remote attacks and prevents unauthorized access from getting a foothold in your secure network. This will enable you to extract data from TOTPs, thumbprint scanners or even Yubikeys and verify the users accessing your cloud network.
Password Policy Enforcement
Another challenge faced while trying to secure a cloud network is the varying standards of all the passwords of all the users who access it. The difference in standards can make breaches easier to happen and there rises a need for standardization of all the password credentials issued to the users of your cloud. But with an IAM solution, you can set the minimum standard required to set a password. With an effective password policy enforcement, you can rest assured that all your critical data is protected irrespective of the number of service providers you are associated with. It consolidates all the applications on your network under a single identity and verifies that all the passwords required to access your network comply with PCI and ISO/IECt standards.
Securing your cloud with an effective Identity and Access Management solution can empower you to control identity and access across your cloud environment. In addition to this, an IAM solution helps you improve data security, privacy, standards compliance, and productivity.