Identity management encompasses several operational mechanisms for managing users across a large system or network of applications. Two of the most prominent of those are Single Sign-on (SSO) and Federated Identity Management. Due to its evolving nature, identity and access management has several terms thrown around ambiguously. Even among developers, major differences are often missed while talking about federated identity and SSO. In this article, we aim to break down the difference between the two.
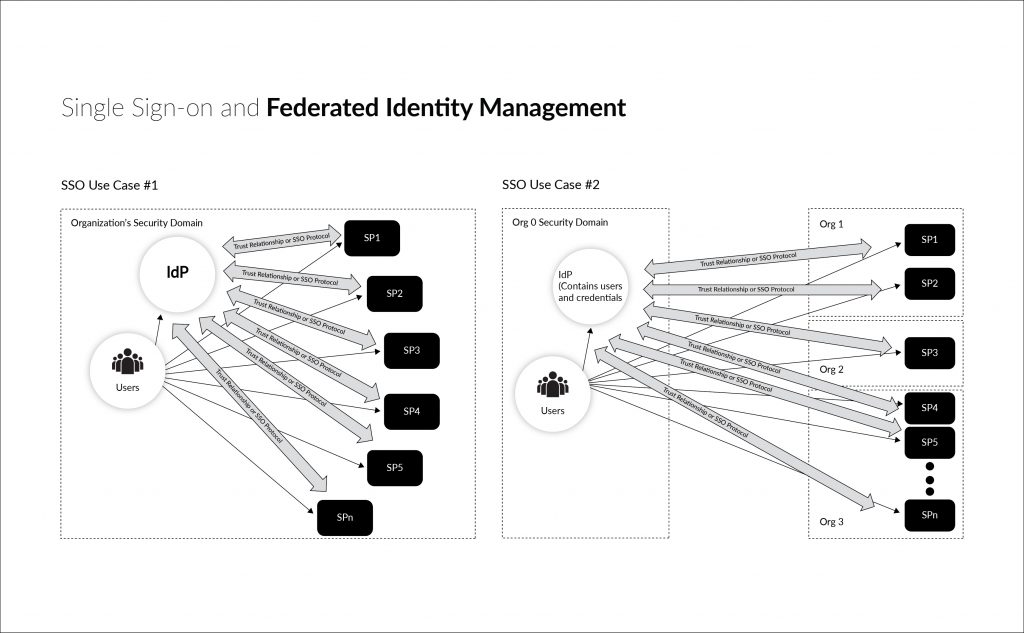
In simple terms, Single Sign-on is a method of authenticating users by using their identity as the key to unlock access to multiple applications within a single organization. Federated identity management, on the other hand, refers to a set of protocols and standards which manages identity between a single Identity Provider and multiple organizations. In federated identity, trust relationships are formed between organizations using digital signatures, encryptions or Public Key Infrastructure (PKI).
Both the systems fall under the Identity and Access Management umbrella, where they are responsible for:
- Authenticating users
- Checking for authorization
- User provisioning
- Audit of identity systems
- User repository management
Single Sign-on
For users of multiple cloud based applications, remembering multiple sets of credentials and also ensuring that all the credentials are kept secure becomes a major challenge. Integrating all these apps into a single platform to access them all with a single set of credentials is exactly what a Single Sign-on (SSO) solution delivers.
A good example of this concept of SSO is Google’s range of apps, where it is possible to access an exhaustive list of applications such as Drive, Sites, Calendar and so on – using only a single authentication with your Gmail ID.
SSO can be achieved using various mechanisms like:
- LDAP server or user directory
- SAML authentication
- Password management systems
The characteristic component of an SSO system is the identity provider. For a general network using SSO, identity is often managed like this:
- User gets authenticated by the Identity Provider (IdP)
- Authenticated user is permitted to access authorized apps and services
- When the user tries to access applications, the application cross verifies the IdP metadata to confirm the user authentication
- The user can then access apps without requiring further individual authentication on each application
Federated Identity Management
When SSO is extrapolated to include applications and networks from other enterprises and security domains, we get federated identity management. The objective of federated identity management is to share an identity through pre-agreed guidelines and rules between two or more organizations and networks. Identities are mapped and managed between several identity providers. Like we mentioned before, trust relationships are established using digital signatures and PKIs.
A few of the common protocols used for establishing a federation relationship are:
- SAML 2
- WS-Federation
- OAuth 2
- OpenID
- WS-Trust
- Custom protocols
Federation can take many forms like:
- Many applications split within the same organization
- Many applications split within different organizations
- Multiple IdPs trusting a single IdP
- A single IdP acting as an identity broker between several ‘user-IdP’ pairs and service providers spread across multiple organizations
A small to mid sized organization will often require their employees to work on a host of applications hosted on their network. Akku from CloudNow Technologies is a highly efficient Identity Provider which provides your network with Single Sign-on. It eliminates the need for your employees to remember multiple passwords, thereby improving the overall security of your network. Be it cloud or on-premise, Akku will seamlessly handle identity management for a large number of users. Get in touch with us to know more.