Google Cloud Platform (GCP) IAM comes as a free service that is available by default to all users of the Google Cloud Platform. GCP IAM is Google’s identity management console, enabling administrators of organizations to manage access and permissions provided to employees across the range of applications and resources that come as part of the Google Cloud Platform. The main function of the IAM is to grant specific users/roles with access to specific GCP resources and prevent unwanted access to other resources.
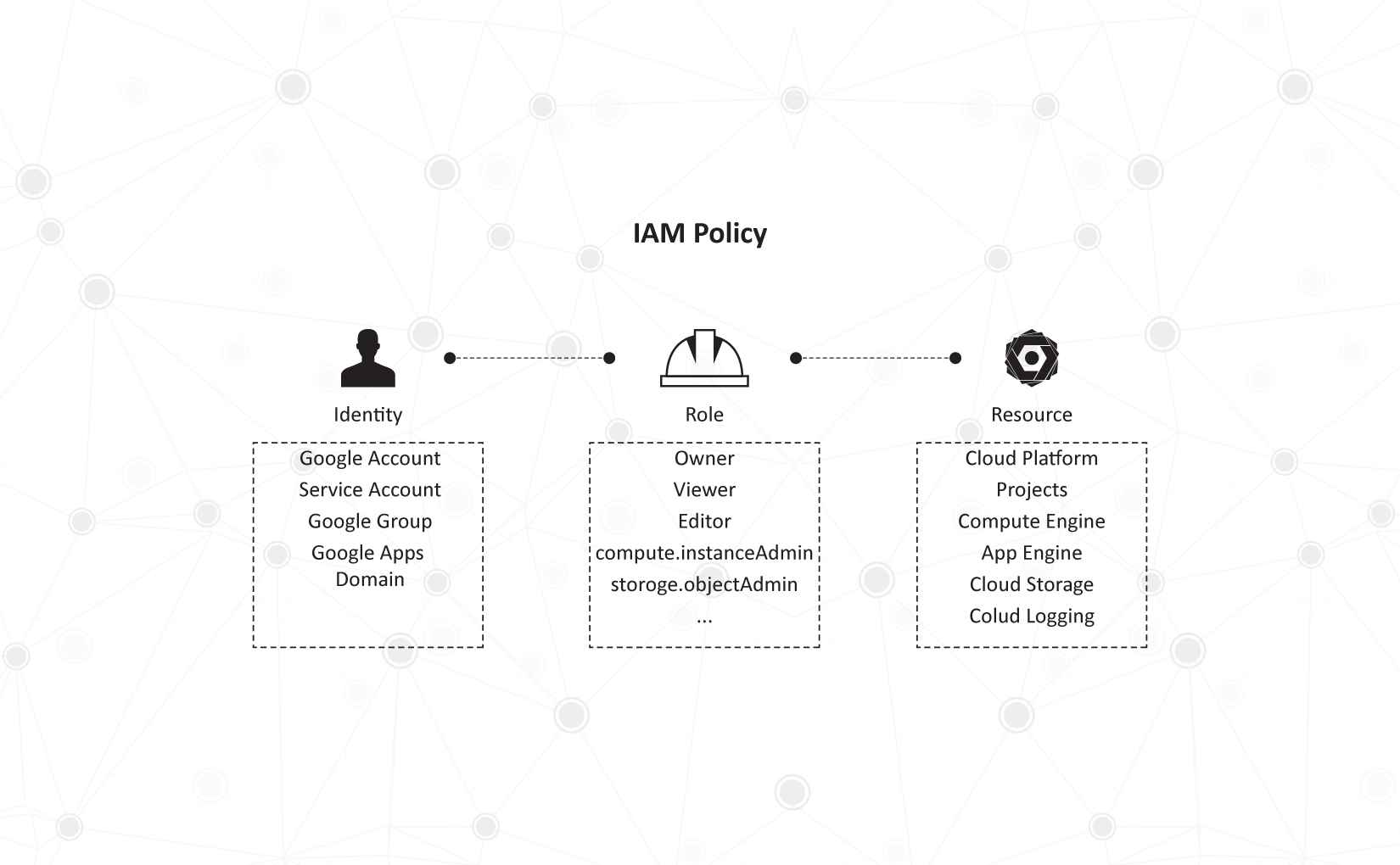
The fundamental building block of GCP IAM is an IAM Policy which answers the question of who (identity) has what access (role) to which data or applications (resource). This IAM Policy is made up of permissions, bundled into roles and matched by identities.
Let’s take a closer look at the concepts of identity, role, and resource as defined by GCP IAM, which make it a useful IAM solution.
Identity
A user’s identity can be accounted for through their Google account (assigned to an individual), Service account (assigned to a service related to the user’s role), a Google group (which can contain more than one Google/Service account), or a G Suite domain name (consisting of all G Suite accounts under a particular domain) or Cloud Identity domain (consisting of all G suite accounts under a particular organization) name.
Role
A role is a combination of permissions assigned to an identity. Traditionally, Google had what are now known as Primitive Roles – which were a standard set of 3 – namely, ‘Owner’, ‘Editor’ and or ‘Viewer’.
However, in GCP IAM, Google has gone not one but two steps further – with Predefined Roles and Custom Roles – in allowing administrators a wider range of options when it comes to assigning roles (and therefore, access to do less or more) to the organization’s resources.
With what are known as Predefined Roles, granular separation of duties, such as Instance Admin and Network Admin to name a few, is made possible. Custom Roles, as the name suggests, are roles which administrators can customize based on the organization’s needs.
Resource
As defined by Google, “resources are the fundamental components that make up all GCP services”, and include Cloud Pub/Sub topics, Compute Engine Virtual Machines, Cloud Storage Buckets, and App Engine Instances.
These resources can then be grouped into projects. Administrators can assign permissions based on different roles to identities in their organization in order to provide them with access to specific resources. On the other hand, they can also provide access to projects, which will then provide users with access to all resources under the project.
In the GCP hierarchy, a group of projects can also be placed under a team, teams can be placed under a department and departments can be placed under the organization. Administrators can decide the level of access they wish to give each user based on this hierarchy.
GCP IAM is great, but….
Despite the extensive control it provides to administrators, and the numerous possibilities in authorizing user access, GCP IAM has one downside.
Organizations today utilize a wide range of applications, not all of them being GCP resources. They may use a combination of resources from Amazon Web Services, IBM or Azure, to name a few, and GCP IAM does not support identity and access management on these resources. Its lack of capability to connect with on-prem identity providers such as Microsoft Active Directory and OpenLDAP is another major roadblock.
Looking for one IAM to manage them all? Try Akku, one of the best identity and access management solutions from CloudNow, that can help you manage identities across your on-premise and cloud-based applications seamlessly!