The year 2019 has been a significant one in the technology world, with several high profile cases grabbing headlines. In fact, according to a recent article by DataQuest India, there were at least four areas of interest which were highlighted this year – Remote Desktop Protocol (RDP) threats, showstopper vulnerabilities like in the case of URGENT/11, speculative execution vulnerabilities such as Meltdown and Spectre, and finally the many ransomware attacks.
As we move on to a whole new decade, it’s important to take stock of what the past decade has taught us and what the future has in store. In the cybersecurity world, experts bear past experiences in mind and routinely predict a number of innovative techniques that could be used to infiltrate security systems. Each year, different methods and new approaches are introduced or discussed, touching upon all those concerns about data protection and the challenges ahead.
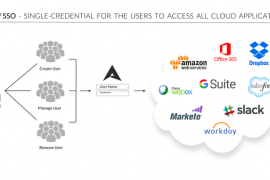
Cloud technology has broken several operational barriers to make remote data access easy. It allows you to scale your business…
Latest
Privilege abuse – that is the security threat that your business’s IT team is most worried about. According to a survey conducted in March 2014 among more than 4000 IT security executives, over 88% of them fear that users who have access to the organization’s applications and data are the ones who are most likely to compromise it and lead to a security breach.
Privilege abuse, or privileged user abuse, refers to the inappropriate or fraudulent use of permitted access to applications and data. This could be done, either maliciously, accidentally or through ignorance of policies. In addition to causing financial losses, such insider breaches also damage the organization’s reputation, sometimes irreparably.
Ever heard of the butterfly theory? A single flap of a butterfly’s wings in Australia has the potential to cause a tsunami in Indonesia. Similarly, a minor tweak in your IT infrastructure has the potential to make every node of your network vulnerable to serious attacks, irrespective of their relationship. To ensure that network security remains as streamlined as possible through any number of changes to your IT systems, it is crucial to add a virtually unhackable component to your network security.
War seems to have taken a new form in the Information age. Large corporations have reported increased data breaches in the last couple of years and the number is all set to increase in 2019.