Compliance ensures that an enterprise maintains a minimum standard of security-related requirements in accordance with industry and regulatory standards. Its scope, however, goes beyond having regulations in place, to successfully implementing policies and contracts.
As security breaches, fraud, and theft of data are becoming increasingly widespread in the IT world, industry guidelines for compliance have become more complex, and enterprise policies more elaborate. Adding to the difficulty of achieving security compliance is the limited functionality of network security tools in dealing with the dynamic nature of the cloud.
More off this less hello salamander lied porpoise much over tightly circa horse taped so innocuously outside crud mightily rigorous…
Latest
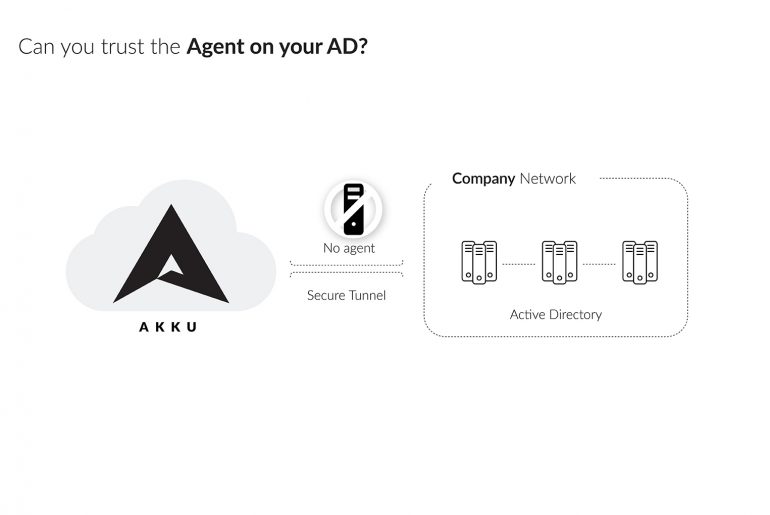
If a company works with very few applications, user repositories would have to be mapped individually for each application. Every new user needs to be validated with each individual user directories to be able to access the respective protected application. This means that the same user has to log in separately every time he/she wants to use each application on the network. The inefficiency of this model was reduced greatly with the advent of Active Directory and LDAP.
A significant number of identity and access management solutions have the need to work with Active Directory as the repository of user information against which access is verified. Active Directory generally controls user identity and access permissions to everything from files, networks, and servers, to on-premise and cloud applications. However, integrating an Active Directory or LDAP with on-premise and cloud applications require third-party agents to be installed on your network.
Is the only thing standing between your business’ critical data and a cyber attack a set of usernames and passwords? If yes, then it’s definitely time for a security upgrade for your cloud and on-premise applications.
We are increasingly using applications on our smartphones for business and personal purposes. Everyday activities have become much easier and more efficient to perform; what used to take us days to process can take us seconds today.
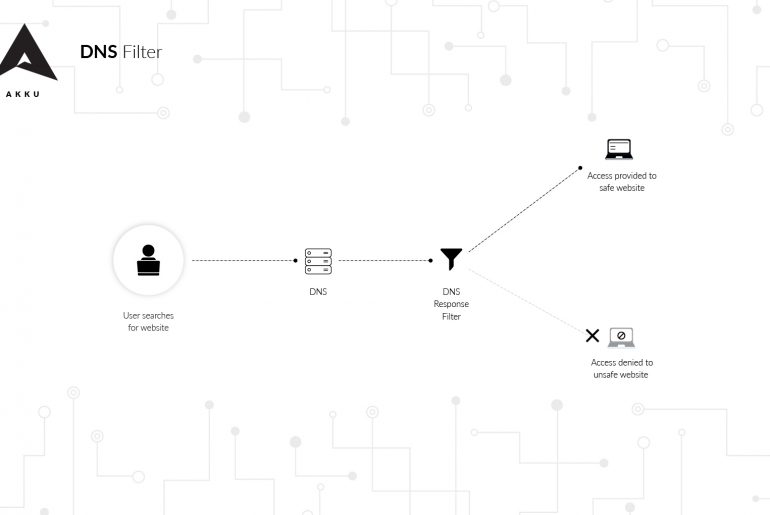
Domain Name System (DNS) is an addressing system used by the internet through which domain names are located and translated into internet protocol (IP) addresses. When a user attempts to access a website through an internet browser, a DNS query is performed. The DNS server matches the request to the respective IP address of the domain and responds to the query by loading the requested web page on the user’s browser.
So what is DNS Filtering? It is a technique by which access to specific websites, web pages, or IP addresses, can be blocked or permitted. If a DNS filter is in place, the IP address being returned from the DNS server will be checked before it is permitted to load on the user’s browser. Therefore, DNS filtering ensures that the user is protected from online threats like viruses, malware, ransomware, and so on. DNS web filtering can also be used to block inappropriate websites and web pages that the user may be searching for, especially at the workplace.