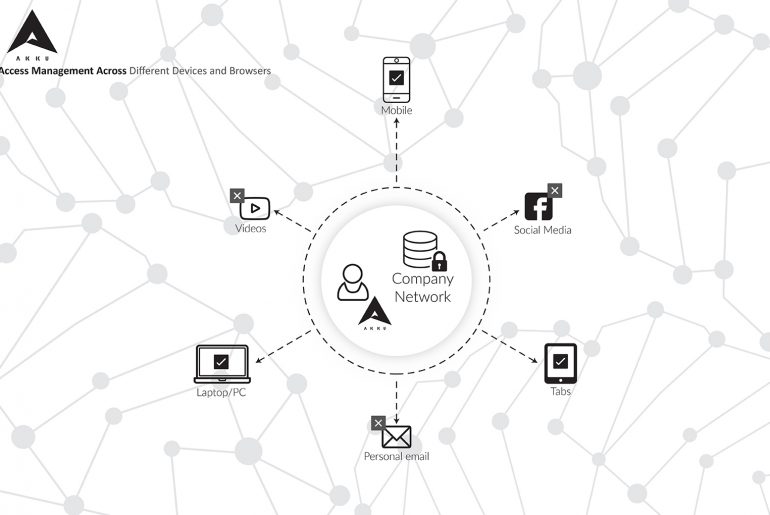
In today’s technology ecosystem, a strong foundation for authorization plays an important role in the overall data security of a company. Controlling each user’s access to data, and monitoring this across devices and browsers is essential to your enterprise’s security.
Implementing a strong device policy is an integral aspect of data security
With a strong device policy in place, it is possible to exercise highly granular control over which of the company’s applications, information, and data your employees can access– through the company’s devices, as well as through their personal devices.
More off this less hello salamander lied porpoise much over tightly circa horse taped so innocuously outside crud mightily rigorous…
Latest
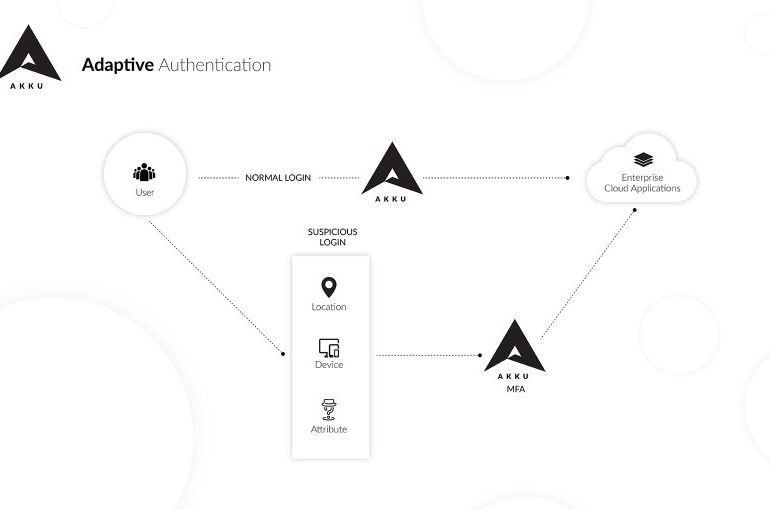
Adaptive authentication, method for enforcing the right authentication factors depending on users profile and tendencies. It acts to balance the level of trust against risk.
Adaptive authentication is the way that two factor authentication or multi factor authentication can be configured or deployed.
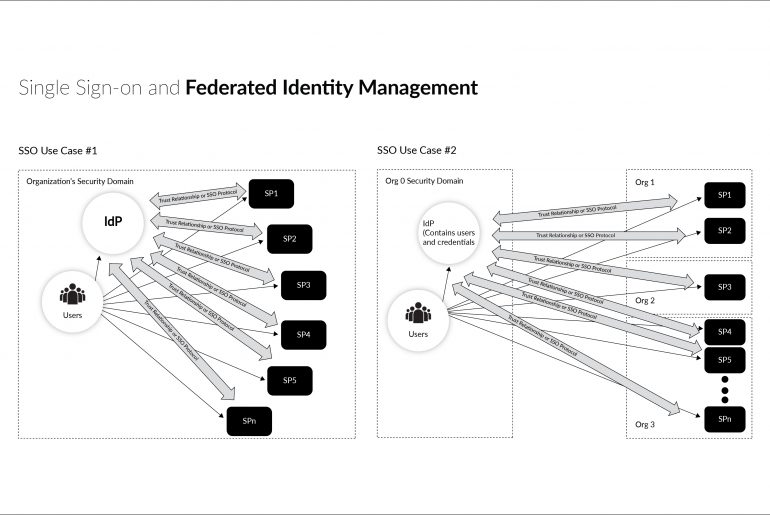
Identity management encompasses several operational mechanisms for managing users across a large system or network of applications. Two of the most prominent of those are Single Sign-on (SSO) and Federated Identity Management. Due to its evolving nature, identity and access management has several terms thrown around ambiguously. Even among developers, major differences are often missed while talking about federated identity and SSO. In this article, we aim to break down the difference between the two.
One of the main reasons for a number of traditional, older enterprises still being wary of cloud computing is the concern they have over the security of their data on the cloud. There are a number of myths surrounding cloud security that make it difficult for many enterprises to take the plunge and undertake cloud migration to leverage the many benefits of the cloud.
Here are a few of these myths, and why you should stop believing them!