Identity and access management, sometimes simply known as identity management, refers to the IT function of maintaining security through the management of digital identities. In a workplace, this includes provisioning employees with accounts to all applications and platforms they will be using for their official tasks, assigning them with the right kind of permissions to each of these applications/platforms, and making sure that the right people have the right access to the right resources and data.
More off this less hello salamander lied porpoise much over tightly circa horse taped so innocuously outside crud mightily rigorous…
Latest
Google Cloud Platform (GCP) IAM comes as a free service that is available by default to all users of the Google Cloud Platform. GCP IAM is Google’s identity management console, enabling administrators of organizations to manage access and permissions provided to employees across the range of applications and resources that come as part of the Google Cloud Platform. The main function of the IAM is to grant specific users/roles with access to specific GCP resources and prevent unwanted access to other resources.
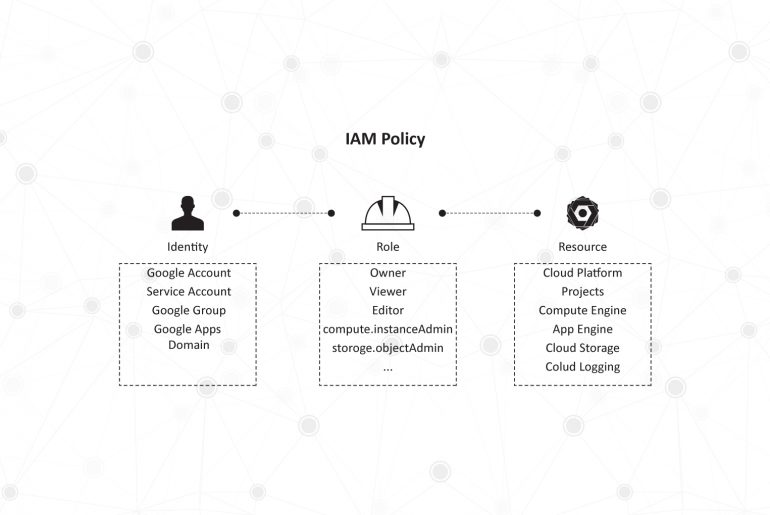
The fundamental building block of GCP IAM is an IAM Policy which answers the question of who (identity) has what access (role) to which data or applications (resource). This IAM Policy is made up of permissions, bundled into roles and matched by identities.
Let’s take a closer look at the concepts of identity, role, and resource as defined by GCP IAM, which make it a useful IAM solution.
Security and privacy of user data are crucial for any organization and is also a major area of risk. So a Secure and Efficient Authentication (SEA) is very important.
How do you make authentication secure and efficient? Let me share some insights on how this can be achieved through certificate-based authentication…
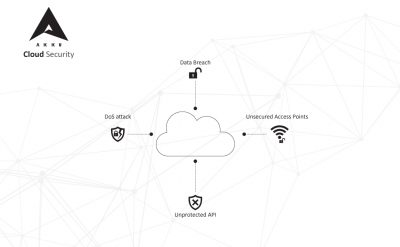
Migration to the cloud is no longer an emerging trend. It is now a well-established method of running the operations of a business. With the cloud, you can manage data and applications in a secure environment and ensure that your users face virtually no latency while using your applications. But although the cloud comes with a basic framework for security, it still has its inherent security risks which need highly specific cloud security solutions to reliably protect your data.
To understand the need for implementing an effective cloud security solution, a deeper understanding of what causes and constitutes a cloud security threat is important.