Today, migrating to the cloud is a crucial stage in a financial enterprise’s growth and development. It is, quite simply, the most efficient way of running operations. With this in mind, financial services organizations are investing significant resources in cloud-based technologies, including infrastructure, platform, and software as a service.
News & Trends
View AllMore off this less hello salamander lied porpoise much over tightly circa horse taped so innocuously outside crud mightily rigorous…
Latest
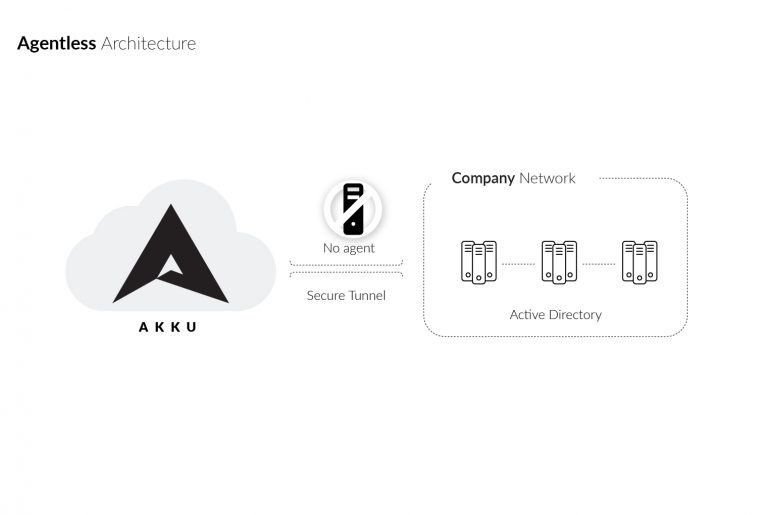
Most IAM tools utilize browser extensions or applications installed on the end-user’s machine, or on an Active Directory, for access to identity. But why?! A user can be identified even without an agent – so having an so-called ‘lightweight agent’ sitting in your Active Directory itself is not the most secure way to manage user identity.
Whenever you create a dependency to achieve a particular solution, it is important to ensure the solution is 100% secure and that applies for the dependencies (Agents) too. This could make the architecture slightly complicated, depending on how it works.
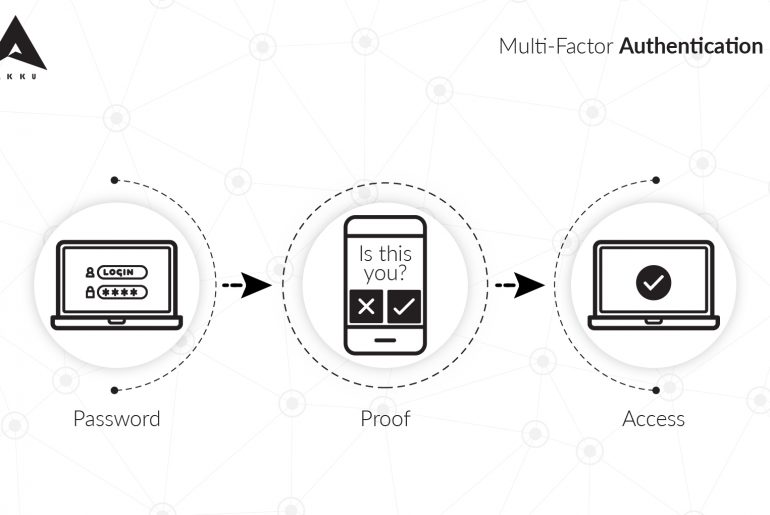
Whether or not you know what it is called, you have likely used 2FA at least once in your life online.
Remember the time you tried logging into your email account from a new device and your email service provider sent you an SMS with a PIN (OTP), to re-validate that it was actually you attempting to login? You would have been allowed access to your inbox only after you entered the correct OTP.
Or the time you tried to transfer money to someone through internet banking. Even though you already entered your customer ID and password, your bank’s application would want to make sure that someone else hadn’t stolen your credentials. They do this by sending you an email with a PIN or a link to click on, for additional validation.
Akku is a great way to control and authenticate communication channels for any enterprise.
One of the biggest threats to any organization is the possibility of a data breach, which can result in loss of data, loss of trust, and ultimately, loss of growth of the business. This makes data security a critical aspect to consider in any enterprise.