In order to protect the digital privacy of European citizens, the European Union created the General Data Protection Regulation to ensure that organizations which collect any personal data from their users make the users aware of how and why their personal data is being used. Essentially, installing an Identity and Access Management solution across your organization for your employees as well as customers can help you stay compliant with this complex regulation.
The EU’s GDPR took effect more than a year ago, but that doesn’t make it any easier to comply with. So if your organization is still finding compliance a difficulty, we are here to help.
More off this less hello salamander lied porpoise much over tightly circa horse taped so innocuously outside crud mightily rigorous…
Latest
At most enterprises, data centers are a repository of information contained within a network of servers from where data is transmitted to other touch points for processing. While these data centers could be cloud-based or on-premise, the security of such business-critical data is of paramount importance.
There could be several vulnerabilities in your network in the form of entry points that seem like they can be ignored. While there are several measures you can implement to physically secure your data center, it takes a lot more to secure remote or even on-premise servers from virtual attacks. An effective data center security solution will allow you to intuitively monitor all the entry points for possible attacks and ensure that you are protected against any breach.
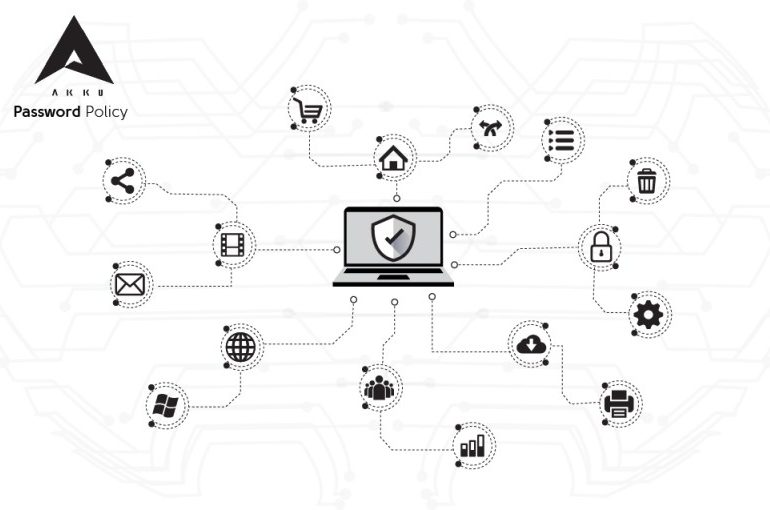
Your password – your secret passphrase or PIN that you use for your email, social media profile, or applications at work – is necessary for you to gain access to your accounts. But more importantly, your password plays a critical role in ensuring that no one else has access to your accounts, ensuring the security and privacy of your own as well as your organization’s data and applications.
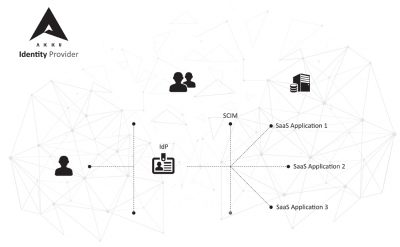
What is SCIM?
The System for Cross-domain Identity Management (SCIM) is an open standard specification, designed to make user management easy. It essentially allows admins of cloud and on-premise networks to move users in and out of their systems quickly and easily. The system builds on inputs from existing user management schemas and allows the integration of powerful authentication models. It uses a common user schema in coordination with an extension model which allows for seamless migration of user data between different nodes of the system.