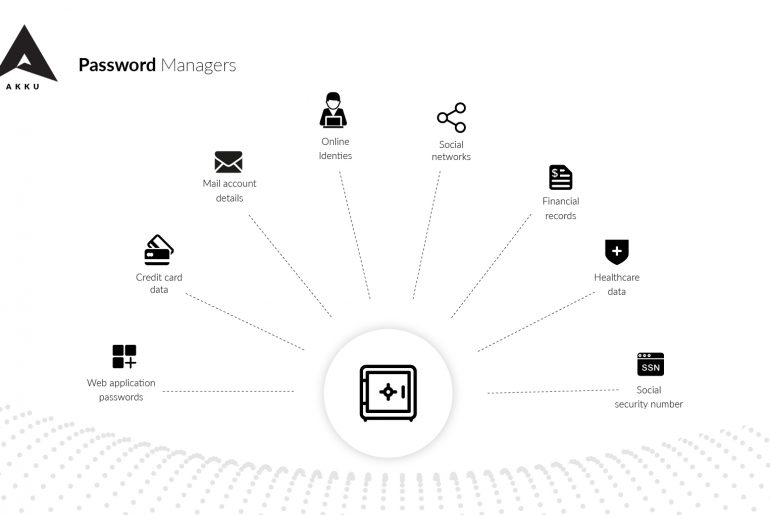
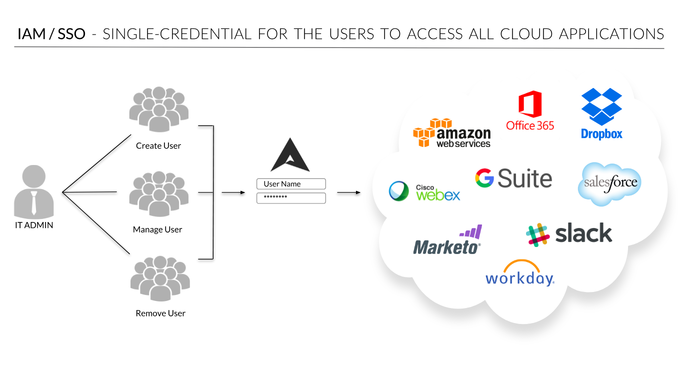
One of the biggest benefits of cloud computing is the level of accessibility it enables – from anywhere, and at any time. However, it is important to set up certain restrictions in order to protect your sensitive applications and privileged user accounts from being compromised.
One such important security measure involves setting up a device policy within your organization.
Latest
More off this less hello salamander lied porpoise much over tightly circa horse taped so innocuously outside crud mightily rigorous…
Identity and Access Management (or IAM) solutions – also known as Identity Management (IdM) solutions – form a critical component of an enterprise’s IT security. And when used with cloud-based applications, they form part of a powerful cloud security set up too.
More off this less hello salamander lied porpoise much over tightly circa horse taped so innocuously outside crud mightily rigorous…