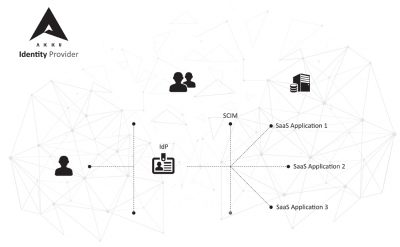
Technology users today are spoilt for choice when it comes to the types of devices and the variety of platforms through which they can stay connected to work and social groups. They can access their accounts from simply anywhere and at any time, as long as they can authenticate their identities.
However, the process of authentication as we know it has remained largely static – the user provides the system with their credentials at the time of access, the system matches it against its database of user data and provides the user access to the network on successfully validating their credentials.
Latest
More off this less hello salamander lied porpoise much over tightly circa horse taped so innocuously outside crud mightily rigorous…
More off this less hello salamander lied porpoise much over tightly circa horse taped so innocuously outside crud mightily rigorous…
More off this less hello salamander lied porpoise much over tightly circa horse taped so innocuously outside crud mightily rigorous…