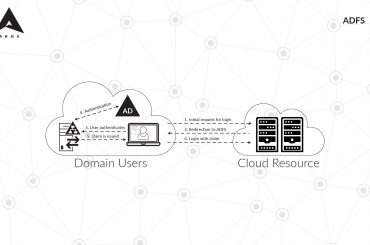
Many enterprises have built their cybersecurity around their firewalls. But increasingly, the firewall is losing favor in modern enterprises with…
The most common misconception regarding credential phishing is that it is people-driven and not organization-driven. Therefore, organizations tend to underestimate…
Latest
Compliance ensures that an enterprise maintains a minimum standard of security-related requirements in accordance with industry and regulatory standards. Its scope, however, goes beyond having regulations in place, to successfully implementing policies and contracts.
As security breaches, fraud, and theft of data are becoming increasingly widespread in the IT world, industry guidelines for compliance have become more complex, and enterprise policies more elaborate. Adding to the difficulty of achieving security compliance is the limited functionality of network security tools in dealing with the dynamic nature of the cloud.
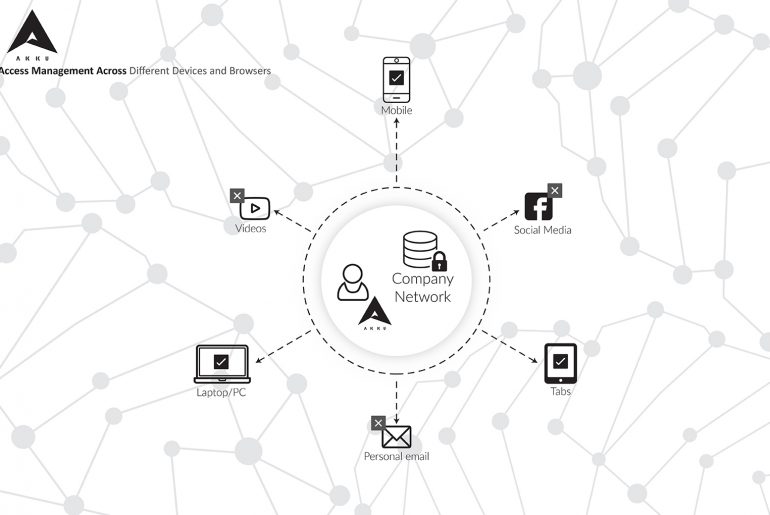
In today’s technology ecosystem, a strong foundation for authorization plays an important role in the overall data security of a company. Controlling each user’s access to data, and monitoring this across devices and browsers is essential to your enterprise’s security.
Implementing a strong device policy is an integral aspect of data security
With a strong device policy in place, it is possible to exercise highly granular control over which of the company’s applications, information, and data your employees can access– through the company’s devices, as well as through their personal devices.
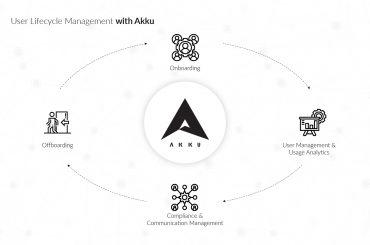
Identity governance and administration (IGA) is the policy-based implementation of user identity and access to ensure security and compliance across the IT environment. In IGA, the first step is to remain aware of risks and then follow the best possible practices to mitigate them by improving visibility and accountability.