Allowing your users to access your official data from anywhere and at any time sounds like a great idea! They can complete their work even when they are on the move by accessing your company’s cloud-based applications. So, why should we restrict access when it has all these pros?
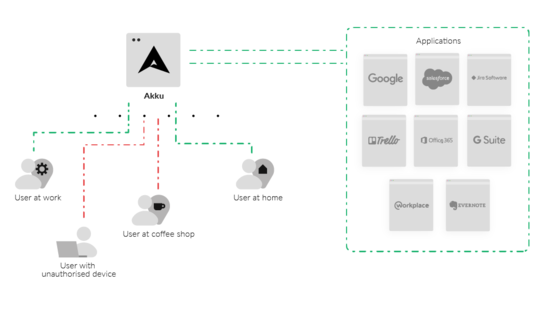
When you permit unshackled access to your company’s applications from any location and device then you also expose your company’s sensitive data and apps to the risk of security or privacy breaches. The possibility of unauthorized access to your sensitive data is a major concern for any company using cloud-based applications.
Why do you need IP restriction?
IP-based access restriction is a great way to secure and protect your mission-critical business data outside your LAN by preventing access to your apps from any IP addresses other than your trusted whitelisted IP ranges.
How does IP-based restriction work?
An IAM solution offering IP-based restriction uses a customized SAML API and integrates with your cloud-based applications. That way, identity management is brought into a common platform across all service providers, with the IAM solution acting as the identity provider. With the identity provider enabling one point control, it is possible to restrict access to your applications only from permitted locations, regulations and IP addresses.
Why restrict based on device?
Device-based access restriction allows you to allow access for specific users only from authorized devices, to prevent misuse or loss of data – that way, users cannot access applications from devices that have not been approved for their use, and unauthorized people cannot access data from devices that may have been approved for other users.
How does device-based restriction work?
With many IAM solutions, device-based restriction is applied through the use of plugins – however more advanced solutions make use of a certificate-based authentication method which has the major advantage of being tamper proof.
A secure certificate-based authentication is completely platform and browser independent and enables cloud administrators to provide or revoke access to SaaS based applications only from specific devices, even when they are outside the office network. Restricting access based on device helps to minimize data breaches and provides the right access to the right people.
Akku offers an IP and device based access restriction feature to help ensure that your data is secure and well protected.