Governments across the globe rely increasingly on technology today to serve their citizens better. But with the rapid evolution of technology, it is often a struggle for the different departments of government to keep up. This happens due to insufficient funds, security concerns or simply a lack of motivation to meticulously plan and implement the move.
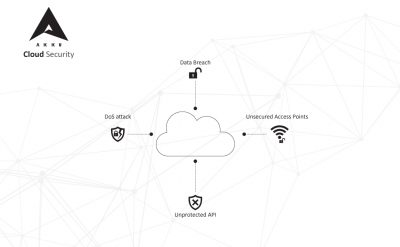
Of these, security is the most critical consideration, since government agencies and departments are possibly the first line of defense against any cyber attack. This is especially true when it comes to government entities wanting to migrate their operations to the cloud.