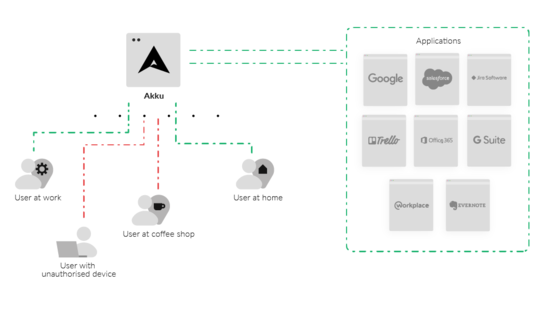
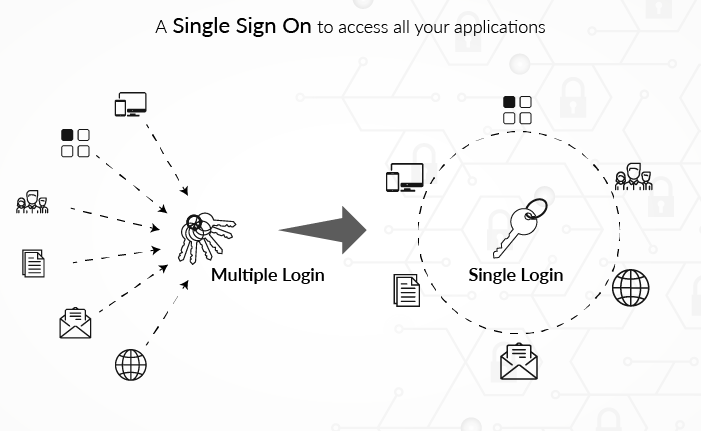
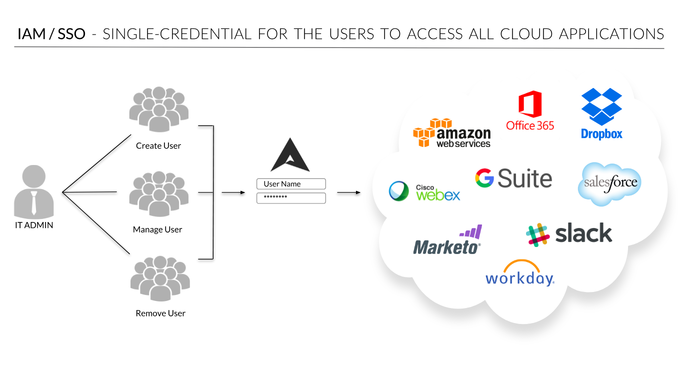
Identity theft is as real as your identity and as dangerous as the one who steals it. It occurs when an unauthorized person or entity uses your personal information to assume your identity and commit fraud and other criminal activities including stealing from you, or from others in your name.
What does an identity thief steal?
Your name, address, credit card or bank account information, and even information that might otherwise seem harmless, such as photographs, information about your family members or your date of birth could be used in harmful ways in the wrong hands.