Remote working has impacted the world of cybersecurity in multiple ways. Remote workers are often not protected by enterprise-level security…
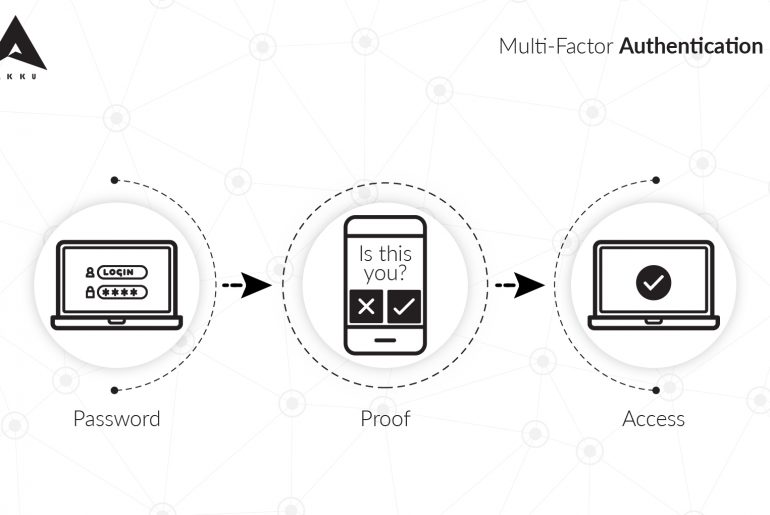
When large organizations like LinkedIn, Twitter and Facebook report password hacks, it throws some light on how vulnerable current systems are, as well as the need for multi-factor authentication. However, multi-factor authentication is shrouded in myths that may prevent organizations from adopting it.
Here, we have addressed a few of the most common myths surrounding multi-factor authentication.
What is WebAuthn?
WebAuthn (Web Authentication API) is a global standard specification for secure authentication on the Web, formulated in 2018 by the World Wide Web Consortium (W3C).
This browser-based API allows user authentication on web applications through the creation of strong “credentials” and user-agent-mediated access to authenticators. This could be either in the form of hardware tokens (like U2F security keys) or in-built modules (biometric readers like Google Hello, Apple Touch ID) in the platform. Web Authn has garnered the support of all leading browsers like Chrome, Firefox, and Edge, and is compatible with all leading platforms.
Multi-factor authentication (MFA) is one of the most highly recommended security measures in this age of brute-force attacks, data breaches and other such cyber attacks. And while some off-the-shelf SaaS applications may already come with a built-in MFA feature, when it comes to a custom-built application or website, businesses have to make the tough decision between reinforced security and the high cost at which it comes.
As mobile phones became more sophisticated, their usage shifted from being communication oriented to application oriented. But phone numbers were never intended to be used as secure identifiers – their purpose is to simply act as subscriber identifiers during call routing. When applications use phone numbers in their login processes, it can give attackers and hackers an advantage.
Here are a few ways in which your OTP can be intercepted by hackers:
“irgvctxmsr” – sounds like gibberish, doesn’t it? But if you were to decrypt this string using a mono-alphabet shift cipher where each letter has been shifted to the right by 4 numbers, you would see that it spells “encryption”!
Protecting critical data and information by encrypting them was first performed by Julius Caesar in 120 BC. The art of encryption has been through several modern shifts, and currently most of the data on the internet is protected using sophisticated encryption algorithms like AES (Advanced Encryption Standard), RSA (Rivest-Shamir-Adlemen), ECC (Elliptic Curve Cryptography) and PGP (Pretty Good Privacy).
A brute-force attack is a type of cybercrime which involves automated hacking activity using bots. The primary aim of a brute-force attack is to crack a password in order to gain access to a user account in an unauthorized manner. Using the automation tool, an attacker repetitively attempts different alpha-numeric combinations at considerable speed – thousands per second – until the user’s password is determined and the account is unlocked.
With the advent of the cloud and the rapid innovations in technology, a brute-force attack has emerged as one of the most common types of outsider attack against web applications.
Privilege abuse – that is the security threat that your business’s IT team is most worried about. According to a survey conducted in March 2014 among more than 4000 IT security executives, over 88% of them fear that users who have access to the organization’s applications and data are the ones who are most likely to compromise it and lead to a security breach.
Privilege abuse, or privileged user abuse, refers to the inappropriate or fraudulent use of permitted access to applications and data. This could be done, either maliciously, accidentally or through ignorance of policies. In addition to causing financial losses, such insider breaches also damage the organization’s reputation, sometimes irreparably.
Ever heard of the butterfly theory? A single flap of a butterfly’s wings in Australia has the potential to cause a tsunami in Indonesia. Similarly, a minor tweak in your IT infrastructure has the potential to make every node of your network vulnerable to serious attacks, irrespective of their relationship. To ensure that network security remains as streamlined as possible through any number of changes to your IT systems, it is crucial to add a virtually unhackable component to your network security.
Whether or not you know what it is called, you have likely used 2FA at least once in your life online.
Remember the time you tried logging into your email account from a new device and your email service provider sent you an SMS with a PIN (OTP), to re-validate that it was actually you attempting to login? You would have been allowed access to your inbox only after you entered the correct OTP.
Or the time you tried to transfer money to someone through internet banking. Even though you already entered your customer ID and password, your bank’s application would want to make sure that someone else hadn’t stolen your credentials. They do this by sending you an email with a PIN or a link to click on, for additional validation.