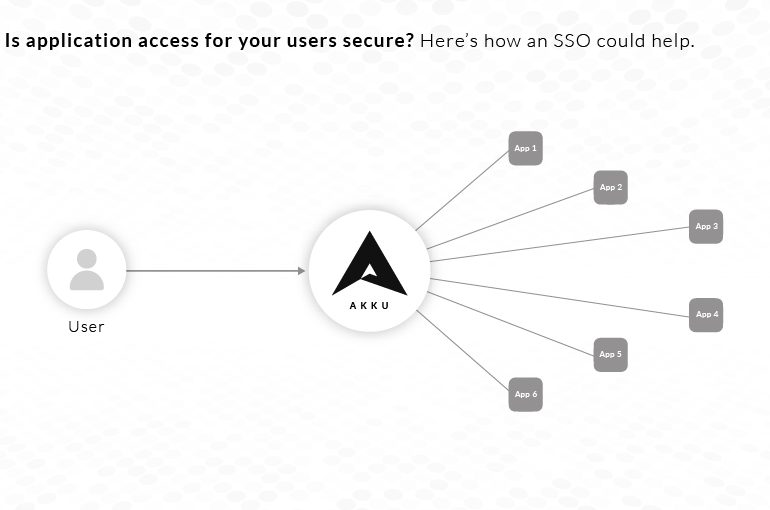
Identity Access Management (IAM) is a collective term that covers processes and policies to manage user identities and regulate user…
In any enterprise, it is a given that employees will come and go, and many will switch roles within the…
When the digital revolution started, media companies were among the first ones to embrace it. Today, most media companies create content targeted exclusively at online subscribers on digital platforms, pivoting their efforts to become more user-friendly for a digital audience.
In order to convert free digital users into paid users, it is also important to effectively profile them and target the right ads to the right users. Therefore, it becomes crucial to learn more about the users logging in to view media content – whether on an online magazine or a video streaming platform. At the same time, user information that is collected online needs to be safeguarded and the methods used for data handling must adhere to strict regulations.
Akku and Okta are both highly efficient cloud security solutions that strive to help companies manage and secure user authentication on applications in their network, and to transform their customer experiences. Here are a few key differences between the features of Akku and Okta.
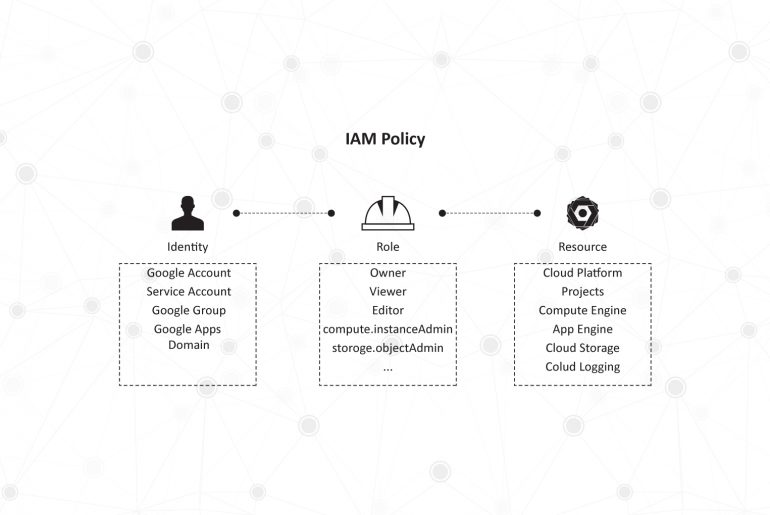
Google Cloud Platform (GCP) IAM comes as a free service that is available by default to all users of the Google Cloud Platform. GCP IAM is Google’s identity management console, enabling administrators of organizations to manage access and permissions provided to employees across the range of applications and resources that come as part of the Google Cloud Platform. The main function of the IAM is to grant specific users/roles with access to specific GCP resources and prevent unwanted access to other resources.
The fundamental building block of GCP IAM is an IAM Policy which answers the question of who (identity) has what access (role) to which data or applications (resource). This IAM Policy is made up of permissions, bundled into roles and matched by identities.
Let’s take a closer look at the concepts of identity, role, and resource as defined by GCP IAM, which make it a useful IAM solution.
Whether or not you know what it is called, you have likely used 2FA at least once in your life online.
Remember the time you tried logging into your email account from a new device and your email service provider sent you an SMS with a PIN (OTP), to re-validate that it was actually you attempting to login? You would have been allowed access to your inbox only after you entered the correct OTP.
Or the time you tried to transfer money to someone through internet banking. Even though you already entered your customer ID and password, your bank’s application would want to make sure that someone else hadn’t stolen your credentials. They do this by sending you an email with a PIN or a link to click on, for additional validation.
At most enterprises, data centers are a repository of information contained within a network of servers from where data is transmitted to other touch points for processing. While these data centers could be cloud-based or on-premise, the security of such business-critical data is of paramount importance.
There could be several vulnerabilities in your network in the form of entry points that seem like they can be ignored. While there are several measures you can implement to physically secure your data center, it takes a lot more to secure remote or even on-premise servers from virtual attacks. An effective data center security solution will allow you to intuitively monitor all the entry points for possible attacks and ensure that you are protected against any breach.
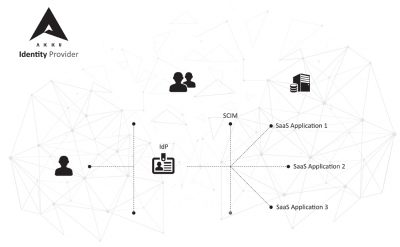
What is SCIM?
The System for Cross-domain Identity Management (SCIM) is an open standard specification, designed to make user management easy. It essentially allows admins of cloud and on-premise networks to move users in and out of their systems quickly and easily. The system builds on inputs from existing user management schemas and allows the integration of powerful authentication models. It uses a common user schema in coordination with an extension model which allows for seamless migration of user data between different nodes of the system.