In any enterprise, it is a given that employees will come and go, and many will switch roles within the…
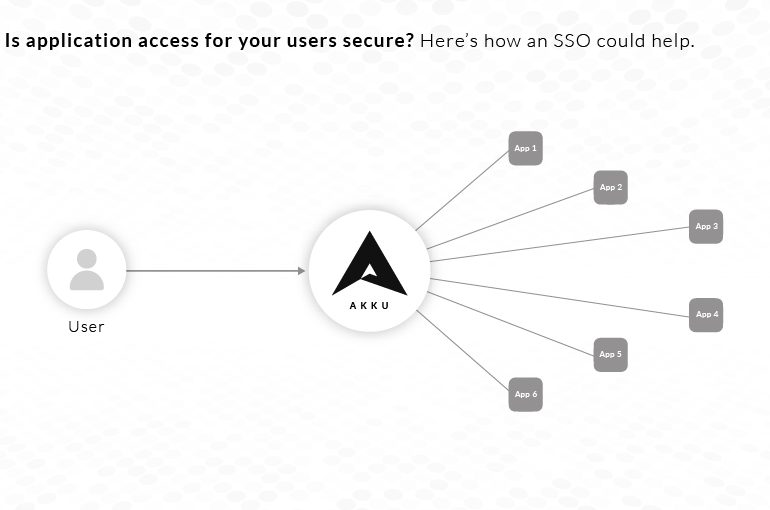
Single Sign-On (SSO) is a session and user authentication service where one set of credentials – typically a username and…
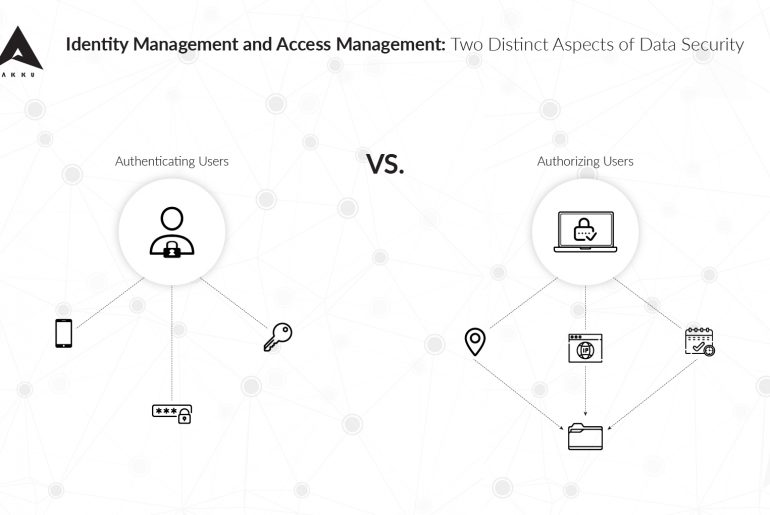
Only a small percentage of people across industries understand the difference between Identity Management and Access Management. The two concepts are certainly related and intricately interwoven, but they are still distinct in meaning and function.
In order to protect the digital privacy of European citizens, the European Union created the General Data Protection Regulation to ensure that organizations which collect any personal data from their users make the users aware of how and why their personal data is being used. Essentially, installing an Identity and Access Management solution across your organization for your employees as well as customers can help you stay compliant with this complex regulation.
The EU’s GDPR took effect more than a year ago, but that doesn’t make it any easier to comply with. So if your organization is still finding compliance a difficulty, we are here to help.
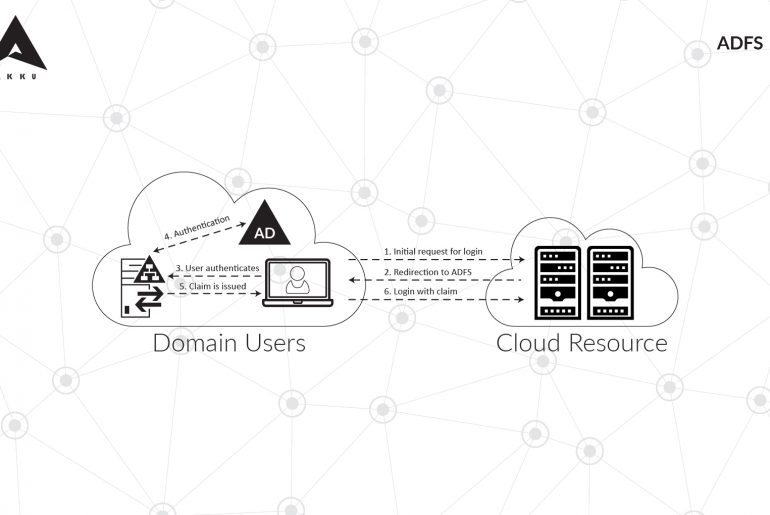
ADFS (Active Directory Federation Services) is an SSO solution created by Microsoft to authenticate users logging into applications which are incompatible with Integrated Windows Authentication (IWA) and Active Directory (AD).
ADFS provides organizations with the flexibility needed to simplify the user experience while improving the control that admins have over user accounts across owned as well as third-party applications. Since ADFS implements SSO, your employees are required to remember only one set of credentials for all the applications.
Social login is a form of single sign-on, where users are allowed to log into an application or website using one of their existing social media account credentials. A social login, therefore, eliminates the need for users to register on yet another online platform – saving them the need to remember yet another set of credentials.
If you are a business, you may have noticed that a social login option on your online platform has had a positive effect on the number of registrations you receive. If you are an individual user, you may have found the option to either “Sign up” or “Login with Facebook/Google” and felt relieved that you were able to access the platform in just a few seconds by choosing the latter. But have you ever thought of how secure this method of login really is?
Apart from data security, data privacy represents a major area of concern in IT security today. When it comes to data privacy, all organizations are very particular about where and how their company data is being saved, and who has access to it.
This is also related to one of the major reasons why organizations still hesitate to move their data to the cloud – “who else has access to my data if I move to cloud?” Even though almost every IaaS and PaaS provider tries to build confidence in their clients through certifications by authorized agencies, many enterprises are still not convinced. The reason is that there are still areas that lack transparency, where details on their data privacy are not clearly explained and conveyed to them.
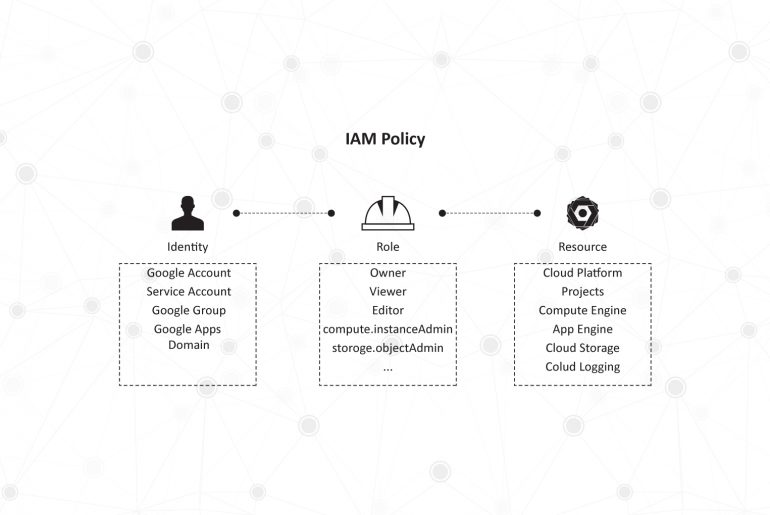
Google Cloud Platform (GCP) IAM comes as a free service that is available by default to all users of the Google Cloud Platform. GCP IAM is Google’s identity management console, enabling administrators of organizations to manage access and permissions provided to employees across the range of applications and resources that come as part of the Google Cloud Platform. The main function of the IAM is to grant specific users/roles with access to specific GCP resources and prevent unwanted access to other resources.
The fundamental building block of GCP IAM is an IAM Policy which answers the question of who (identity) has what access (role) to which data or applications (resource). This IAM Policy is made up of permissions, bundled into roles and matched by identities.
Let’s take a closer look at the concepts of identity, role, and resource as defined by GCP IAM, which make it a useful IAM solution.
Security and privacy of user data are crucial for any organization and is also a major area of risk. So a Secure and Efficient Authentication (SEA) is very important.
How do you make authentication secure and efficient? Let me share some insights on how this can be achieved through certificate-based authentication…
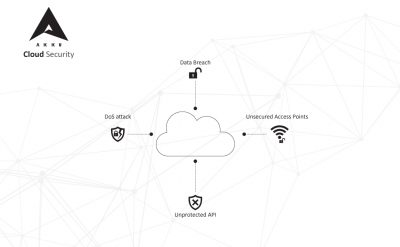
Migration to the cloud is no longer an emerging trend. It is now a well-established method of running the operations of a business. With the cloud, you can manage data and applications in a secure environment and ensure that your users face virtually no latency while using your applications. But although the cloud comes with a basic framework for security, it still has its inherent security risks which need highly specific cloud security solutions to reliably protect your data.
To understand the need for implementing an effective cloud security solution, a deeper understanding of what causes and constitutes a cloud security threat is important.