Whether or not you know what it is called, you have likely used 2FA at least once in your life online.
Remember the time you tried logging into your email account from a new device and your email service provider sent you an SMS with a PIN (OTP), to re-validate that it was actually you attempting to login? You would have been allowed access to your inbox only after you entered the correct OTP.
Or the time you tried to transfer money to someone through internet banking. Even though you already entered your customer ID and password, your bank’s application would want to make sure that someone else hadn’t stolen your credentials. They do this by sending you an email with a PIN or a link to click on, for additional validation.
This is exactly what 2FA or two-factor authentication solution is all about.
Known by many names – two-factor authentication, two-step authentication, two-step verification or dual factor authentication, 2FA refers to a second level of authentication added on in order to enhance security inherent to a login process. This is in addition to the username and password step, which is relatively susceptible to hacking.
When two or more layers are added to the login authentication process, it’s also known as multi-factor authentication or MFA.
Types of MFA security
A two or multi-factor authentication process typically asks you for ‘something you know’ in the first step, such as your email ID/username and password.
In the second step, it may ask you to authenticate your identity with ‘something you have’ or ‘something you are’.
Something you know – the knowledge factor:
This could be your username and password, as in any ordinary login process, or it could be a PIN.
Something you have – the possession factor:
This traditionally referred to hand-held token items, such as smart cards or Yubikeys embedded with a certificate to identify the user. Nowadays, a ‘possession’ could also be your smartphone, containing an app which sends a push notification or a TOTP. This is especially beneficial since tokens like smart cards are relatively more prone to being lost, stolen or misplaced.
Something you are – the inherence factor:
Biometric authentication could involve the scanning of a biological element that is exclusively yours – such as your fingerprint, hand geometry, retina, iris and so on. Voice recognition can also be used.
Two-factor authentication for your business
If your business relies on highly sensitive data or handles personal data of clients, you need to have an information security management system in place. This is especially crucial these days as several governments are imposing stringent regulations to ensure that the privacy of their citizens is not compromised. Some business standard certifications also require security compliances to certify your business and, therefore, it is important for you to protect sensitive data with more than just single-factor authentication (SFA).
By setting up 2FA or MFA security in all your business applications, you are assured of a higher degree of protection. In this manner, even if somebody does steal, guess or hack a password or even a list of passwords, through a brute force attack, they will be stopped at the second level as they attempt to log in to a specific individual’s account.
Multi-factor authentication solutions by Akku
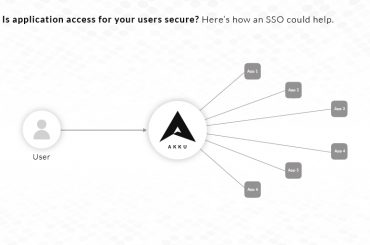
When your business uses multiple applications, it may be both expensive and difficult to set up and streamline multi-factor authentication in each. That is where Akku comes in, with the promise to address all these concerns once and for all.
Once you opt for Akku, it becomes a common identity provider (IdP) across all your enterprise applications and creates a single sign-on (SSO) page through which your users can access them. Having brought all of your applications to a single platform through the SSO, Akku then seamlessly implements the multi-factor authentication functionality across them all.
With Akku, users can decide to use any of the following options as their second factor for re-validating their identity, giving them the power of choice:
-
- A push notification delivered to their smartphone through the Akku mobile app
-
- A time-based OTP (TOTP) which expires in 30 seconds through an authentication app (such as Google authenticator)
- A PIN sent through an SMS to their registered mobile number
Interested to know more? Visit www.akku.work or get in touch with us through sales@akku.work