As organizations increasingly place their data and applications across multiple locations on the cloud, zero trust security is rapidly gaining ground as the network security model of choice among enterprises.
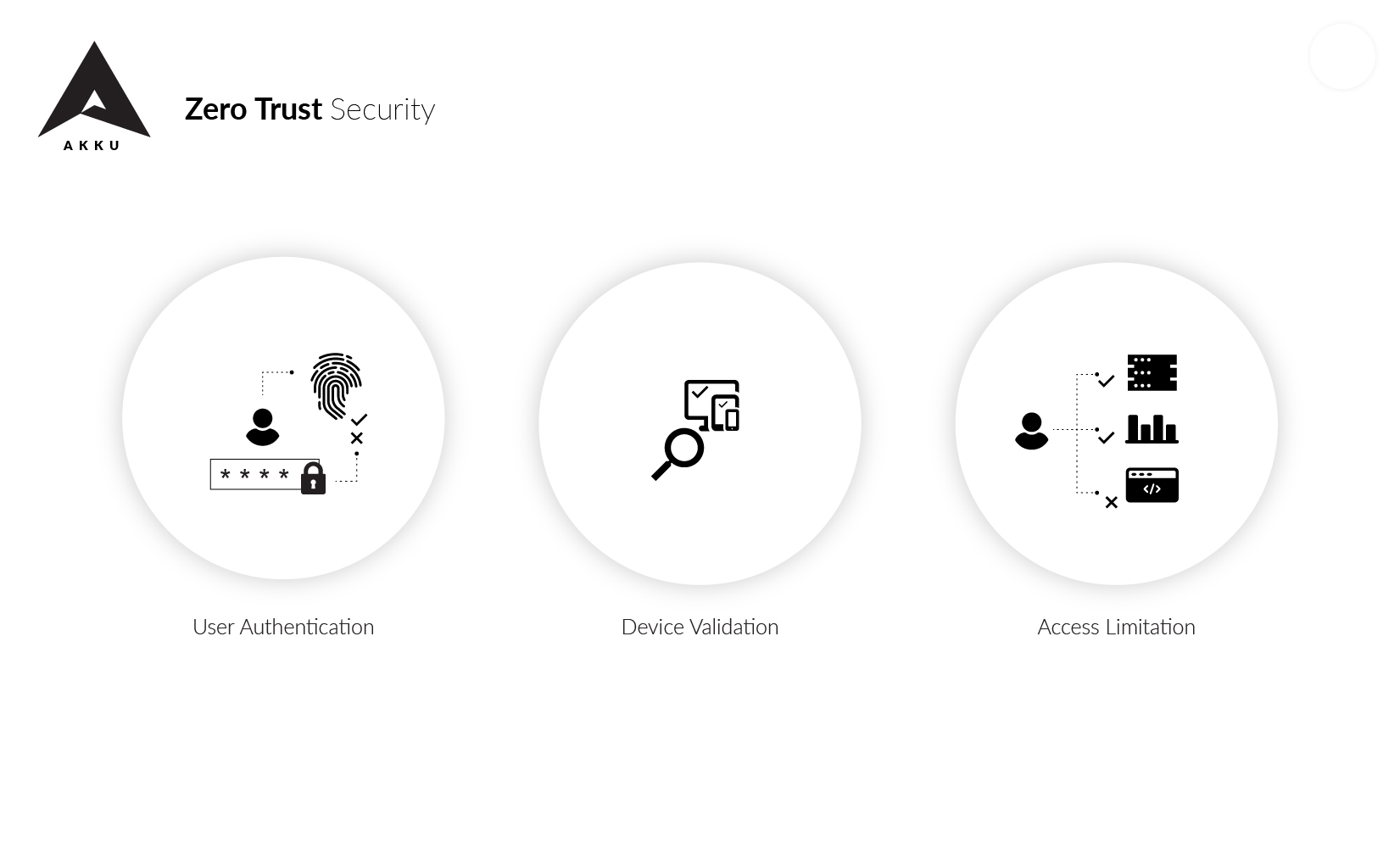
Zero Trust Security is a security model in which a user, irrespective of whether he/she is within or outside the network perimeter, requires an additional verification to get access into a network. There is no particular technology or software product associated with this security model. It simply requires an additional security layer to verify users. This could be anything from biometric verification like thumb-print scanning, or a digital signature verification. Of the two, biometric verification is preferable as it can neither be recreated nor hacked.
Traditionally, organizations have been using what is referred to as the castle-and-moat approach to network security. In this model, the network is the ‘castle’ which is protected by security solutions as a ‘moat’. With this approach, part-of-the-network users were blindly trusted and allowed to enter the castle. However, as companies grew, their data and applications grew with them and the need to split them and store them in multiples silos rose. It also became easier for hackers to gain entry into a “protected” network by accessing a single user’s credentials.
Instead of the castle-and-moat model, adopting the zero trust security model and adding an additional layer of security to a network has been shown to prevent instances of data breaches.
Principles behind zero trust security
1. Trust no one: The model assumes that all the users of the network are potential attackers and hence, no users or systems are to be automatically trusted.
2. Least-privilege access: The users are given access based on a need-to-use basis and nothing more. This can eliminate each user’s exposure to vulnerable parts of a network.
3. Microsegmentation: The entire network is split into segments, each with its own authentication process.
4. Multi-factor authentication: Access to the network requires additional evidence that the user is legitimate.
The network of an organization is its gold mine and most organizations are increasing their spend on network security. Implementing a zero trust security model can go a long way in protecting your network from breaches.
Akku from CloudNow is an intelligent security solution which helps you enforce a zero trust security policy. To know more about its features and how it can benefit your organization’s network security, get in touch with us now.